Welcome to a 5 part series on Recon with ProjectDiscovery! * Part 1 * Part 2 * Part 3 * Part 4 * Part 5 *
Live Host Discovery
After gathering all available subdomains, the following process filters all valid ones based on their HTTP method and response content. The httpx tool can collect information about a web server, such as the types of HTTP methods it supports and the contents of its HTTP headers.
Httpx
During reconnaissance, httpx can gather information about a web server. This information can help identify vulnerabilities and weaknesses in the server. It has various features and options that can be useful for filtering valid subdomains, viewing response headers, identifying HTTP methods, and showing the subdomain's IP.
Also, httpx can be used with subfinder to get fast results.
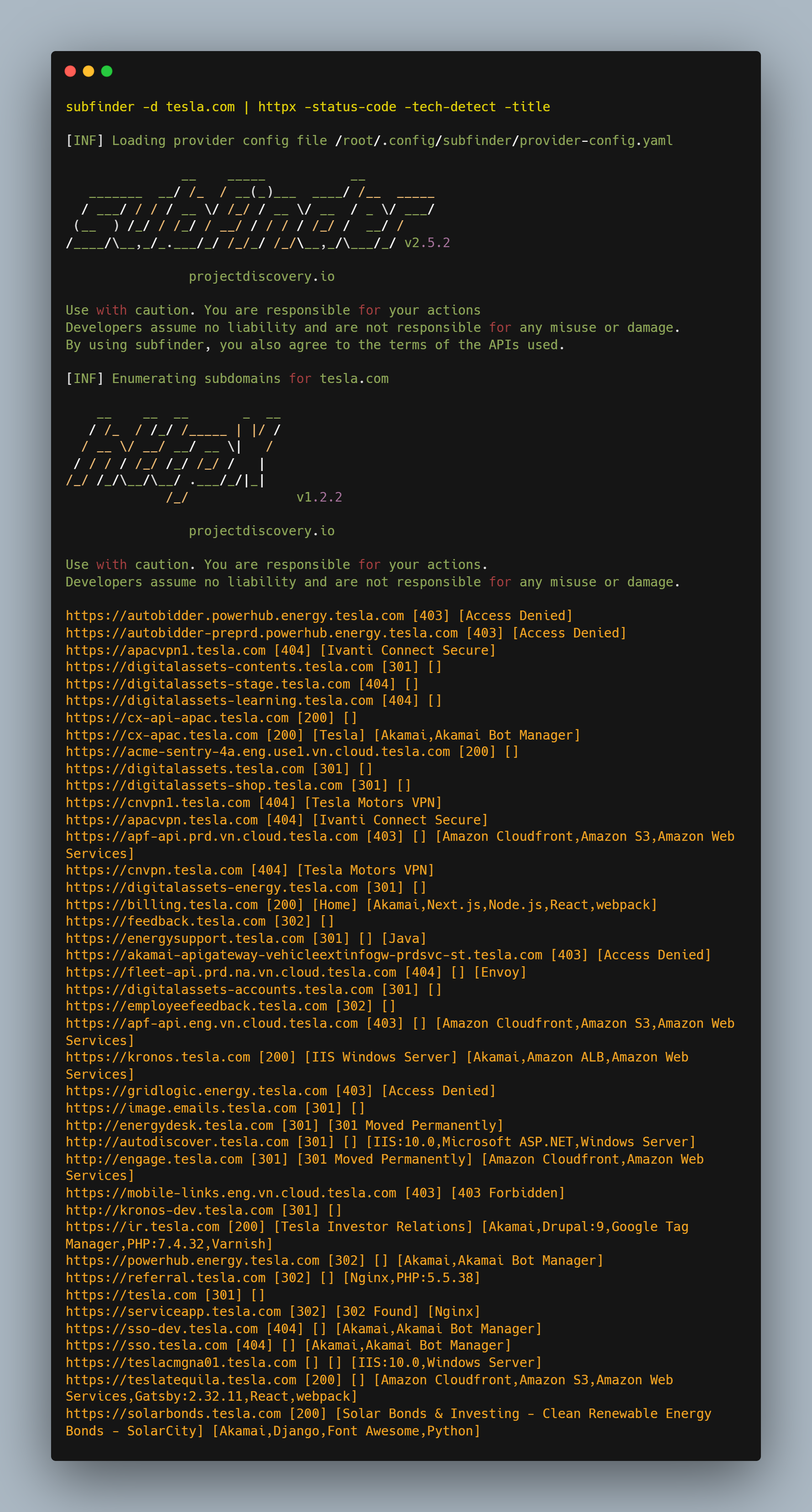
Command: subfinder -d target.com | httpx -status-code -tech-detect -title
-status-code is used to specify the HTTP status code that is returned-tech-detect allows you to identify the technologies & frameworks used-title allows you to extract the title of a webpage from the HTML source code
We can also pipe together subfinder and httpx like this:
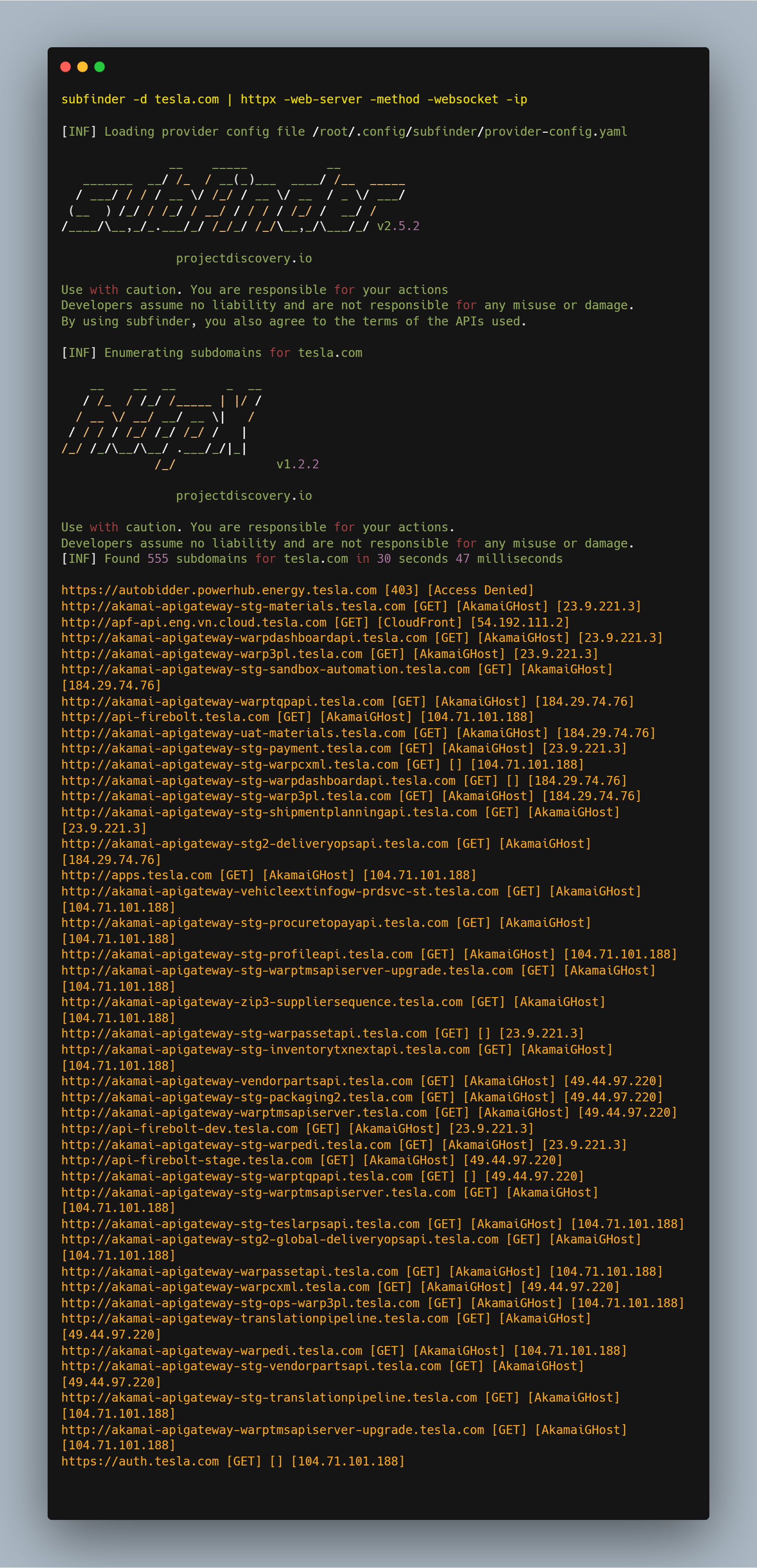
subfinder -d target.com | httpx -web-server -method -websocket -ip
-web-serverallows you to identify the web server software that is being used-method allows you to specify the HTTP method that should be used -websocket displays the server using websocket.-ip displays the IP of the subdomain.
Port Scanning
Port scanning is a technique that can be used as part of reconnaissance to identify which network ports are open on a target system or network. This is a form of active reconnaissance. Network ports are used to identify and differentiate different types of network traffic, and each port is associated with a specific service or application.
By performing a port scan, it is possible to gather information about which services and applications are running on a target system or network and the operating system and version of the target system. This information can be helpful for defensive and offensive purposes, such as identifying potential vulnerabilities or identifying potential targets for an attack.
Naabu
naabu is a tool written in the Go programming language that can quickly and reliably identify open ports on a target system or network. It performs SYN/CONNECT scans on the target system and lists all ports that return a reply, providing information about the services and applications running on the system.
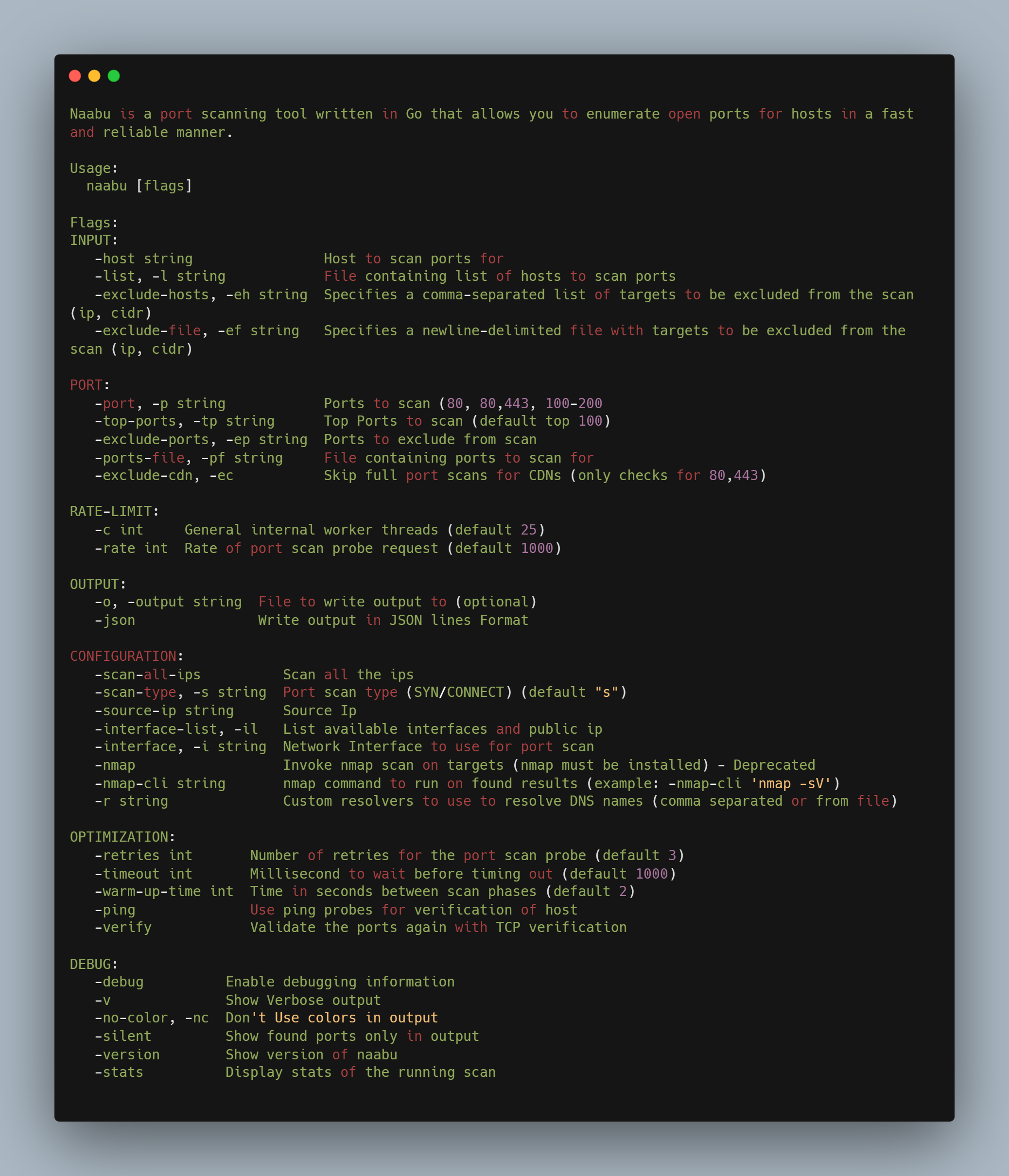
Command: naabu -h (To get all available options)
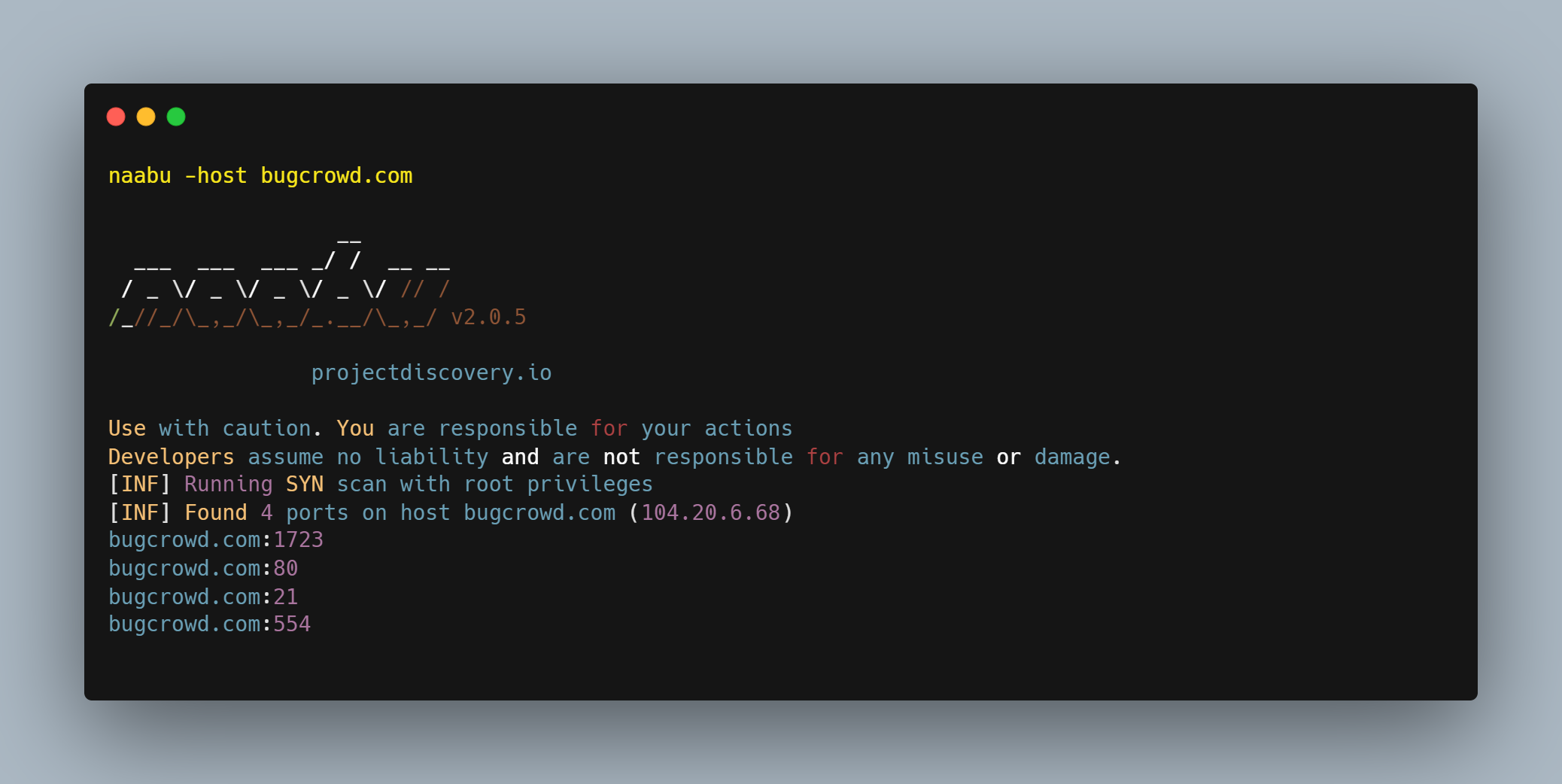
Command: naabu -host target.com (Host to scan ports for)
Author: Harsh Bothra, @harshbothra_
ProjectDiscovery Reconnaissance Series
Reconnaissance is an essential part of penetration testing and bug bounty hunting, as it is the process of gathering information about a target to identify potential attack vectors and vulnerabilities. This blog series provides an overview of the various reconnaissance techniques available, as well as advice on how to effectively utilize them to maximize the chances of success.
- Reconnaissance 101: A Deep Dive in Active & Passive Reconnaissance
- Reconnaissance 102: Subdomain Enumeration
- Reconnaissance 103: Host and Port Discovery
- Reconnaissance 104: Expanded Scanning
- Reconnaissance 105: Additional Types of Active Reconnaissance
Additional Resources & Further Reads
- https://blog.projectdiscovery.io/building-one-shot-recon/
- https://securitytrails.com/blog/tag=reconnaissance
- https://www.bugcrowd.com/resources/levelup/doing-recon-like-a-boss/
- https://www.cobalt.io/blog/scope-based-recon-smart-recon-tactics
- https://www.offensity.com/en/blog/just-another-recon-guide-pentesters-and-bug-bounty-hunters/
- https://infosecwriteups.com/recon-methodology-for-bug-hunting-e623120a7ca6?gi=a63b0a78d505







