Welcome to a 5 part series on Recon with ProjectDiscovery! * Part 1 * Part 2 * Part 3 * Part 4 * Part 5 *
Subdomain enumeration is an essential reconnaissance technique in the fields of penetration testing and bug bounty hunting. In this part of our series on reconnaissance, we will explore the importance of this technique, how it works, and which tools can be used to conduct subdomain enumeration. We will also discuss best practices and common pitfalls to avoid when performing this type of reconnaissance. By the end of this blog, readers will have a more in-depth understanding of subdomain enumeration and how to effectively use it as a reconnaissance technique.
The first thing to think about is active vs. passive subdomain enumeration. We discussed both types of reconnaissance in our previous post, and subdomain enumeration can be either active or passive, depending on the techniques and tools used.
Active subdomain enumeration involves actively interacting with the target domain to enumerate (i.e., identify and list) its subdomains. This can include techniques such as using tools to send DNS requests to the target domain's name servers and analyzing the responses, or using web crawlers to discover subdomains by following links within the target domain.
On the other hand, passive subdomain enumeration involves gathering information about the target domain's subdomains from publicly available sources without actively interacting with the domain itself. This can include techniques such as analyzing the target domain's DNS records and looking for publicly available documents/databases that mention subdomains of the target domain. Active methods are riskier and more ethical than passive subdomain enumeration.
Subfinder
subfinder is a subdomain enumeration tool written in the Go programming language. subfinder is a subdomain discovery tool that returns valid subdomains for websites using passive online sources. It has a simple, modular architecture and is optimized for speed. subfinder is built for doing passive subdomain enumeration, and it does so very well.
Command: subfinder -d target.com
Once you input the command, it will start gathering all available subdomains at a breakneck speed.
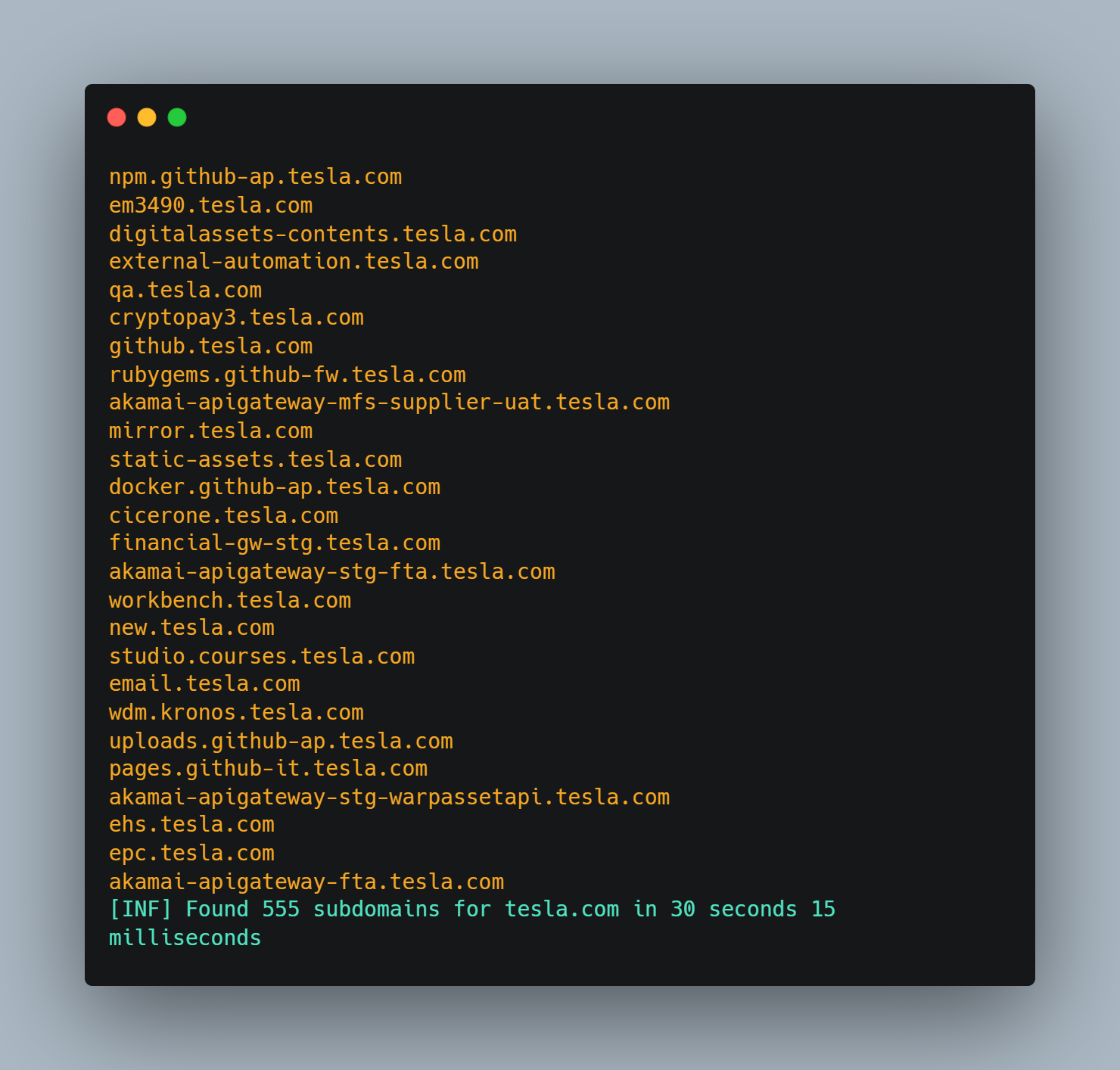
As you can see in the results, the subfinder has found 500+ subdomains in just 30 seconds, which is a very efficient result while performing the reconnaissance.
Subfinder is a tool that allows you to quickly and efficiently find subdomains of a given domain. It is designed to be fast, providing results within a minute or less in numerous instances. One of the critical features of a subfinder is that it uses only the passive method of subdomain enumeration. It does not actively connect to the target domain.
Instead, it simply gathers information from publicly available sources and presents it to the user. This makes it a relatively stealthy tool, as it does not leave any noticeable traces or logs on the target domain.
Click here for a deeper dive on Subfinder.
Amass
amass is a free and open-source tool for network mapping and attack surface discovery that gathers data using active reconnaissance and external asset discovery (passive reconnaissance) methods. This tool focuses on DNS, HTTP, and SSL/TLS data discovery and scrapping.
Command: amass enum -d target.com
Once you input the command, it will start gathering all available subdomains at a slow pace.
Subdomain Brute Forcing
Subdomain brute forcing is a technique used to discover subdomains of a given domain by systematically connecting to many subdomains and seeing which ones are valid. This is typically considered to be active reconnaissance because you will likely end up sending large numbers of DNS requests to the organization's DNS server. Subdomain brute forcing involves using a list of common subdomain names and attempting to connect to them by appending them to a target domain. The success or failure of these connections is used to determine which subdomains are valid.
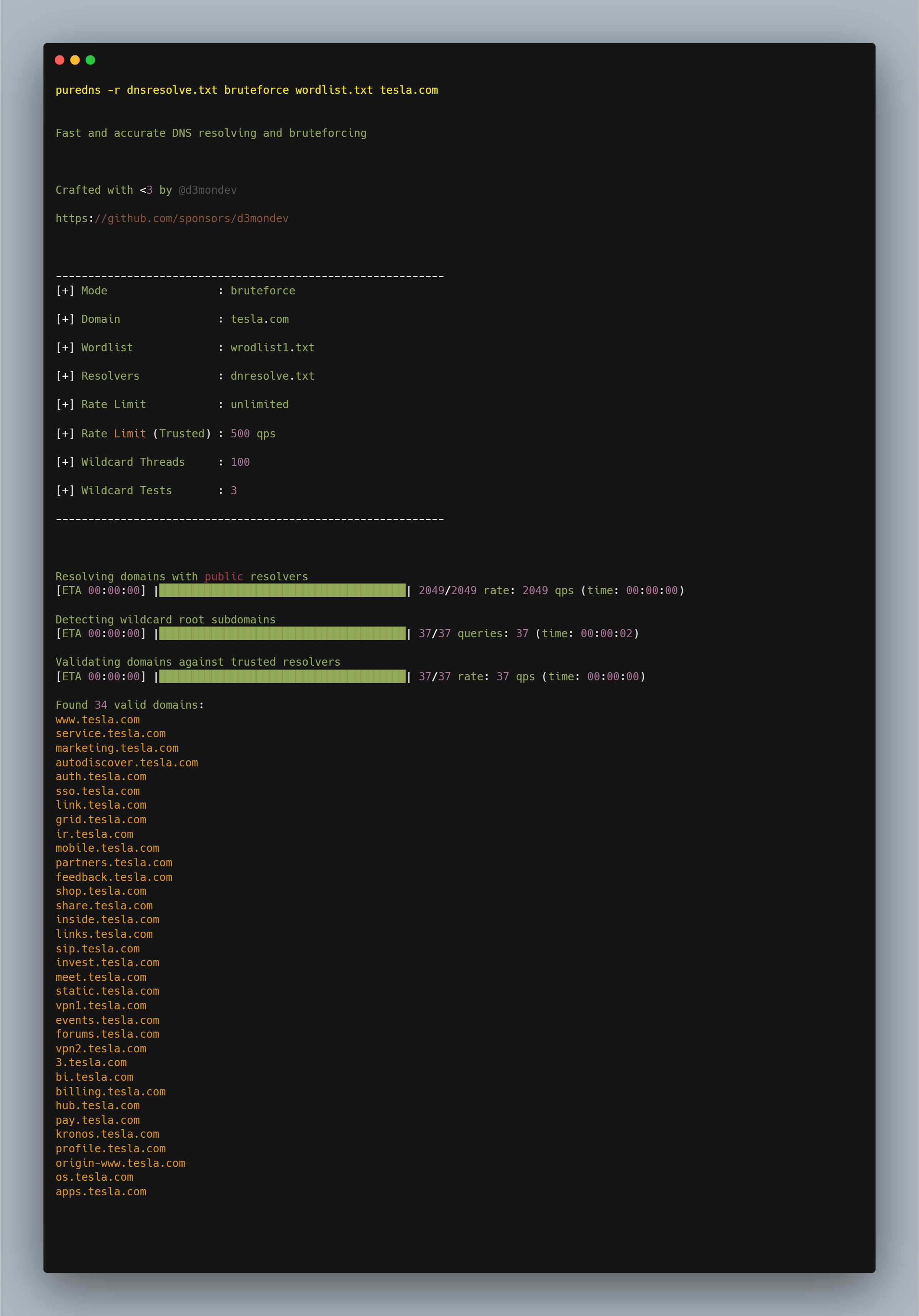
Puredns
puredns is a fast domain resolver and subdomain brute forcing tool that can accurately filter out wildcard subdomains and DNS-poisoned entries.
To perform large numbers of DNS lookups efficiently, puredns uses massdns, a robust stub DNS resolver. Unfortunately, the accuracy of the massdns findings depends on the public resolvers' responses. False positives from wildcard subdomains and incorrect DNS responses frequently spoil the results.
Command: puredns -r dnsresolve.txt bruteforce wordlist.txt target.com
-r to specify the location of a file containing a list of DNS resolvers.wordlist.txt contains all the words for subdomain brute-forcing.
In the next post in this series, we'll look at discovering live hosts and open ports as the next step in a reconnaissance pipeline
Author: Harsh Bothra, @harshbothra_
ProjectDiscovery Reconnaissance Series
Reconnaissance is an essential part of penetration testing and bug bounty hunting, as it is the process of gathering information about a target to identify potential attack vectors and vulnerabilities. This blog series provides an overview of the various reconnaissance techniques available, as well as advice on how to effectively utilize them to maximize the chances of success.
- Reconnaissance 101: A Deep Dive in Active & Passive Reconnaissance
- Reconnaissance 102: Subdomain Enumeration
- Reconnaissance 103: Host and Port Discovery
- Reconnaissance 104: Expanded Scanning
- Reconnaissance 105: Additional Types of Active Reconnaissance
Additional Resources & Further Reads
- https://blog.projectdiscovery.io/building-one-shot-recon/
- https://securitytrails.com/blog/tag=reconnaissance
- https://www.bugcrowd.com/resources/levelup/doing-recon-like-a-boss/
- https://www.cobalt.io/blog/scope-based-recon-smart-recon-tactics
- https://www.offensity.com/en/blog/just-another-recon-guide-pentesters-and-bug-bounty-hunters/
- https://infosecwriteups.com/recon-methodology-for-bug-hunting-e623120a7ca6?gi=a63b0a78d505







