We are thrilled to bring you the new Nuclei v2.3.0! With this release, the entire core has seen a refactor and overhaul, focusing on modularity and future-proofing by adding the unit tests and integration tests.
The release also comes with many exciting new features. Some massive ones being headless support, TCP support, file support for local filesystem templates. Reporting modules have been added for Jira, Github, Gitlab, and many more along the way. The workflow system has been written from scratch with a focus on speed. Configuration files have arrived in Nuclei, allowing you to work with multiple Nuclei customizations for your different needs. A new clustering module has been added to identify identical HTTP requests and send a single request for them, reducing the scan time for large-scale scans. Offline HTTP support has been added too, for parsing raw HTTP responses from the disk and running templates on them!
Headless Requests
Headless support has been added to Nuclei, allowing the users to model the most complex of headless, browser-based interactions in an automated way. This opens up a whole new space of checks for Nuclei. DOM-based vulnerabilities like prototype pollution, DOM-XSS, etc., can be easily automated by users with Nuclei's headless mode.
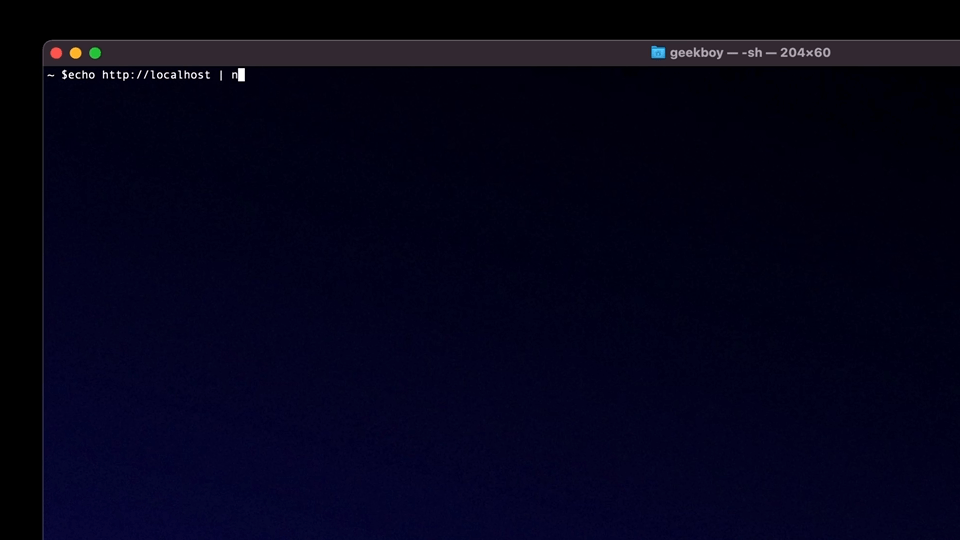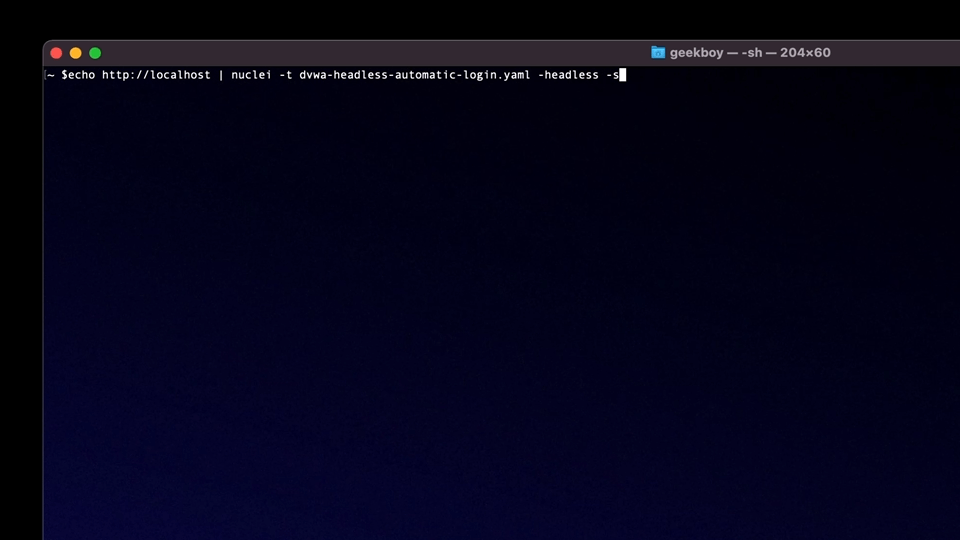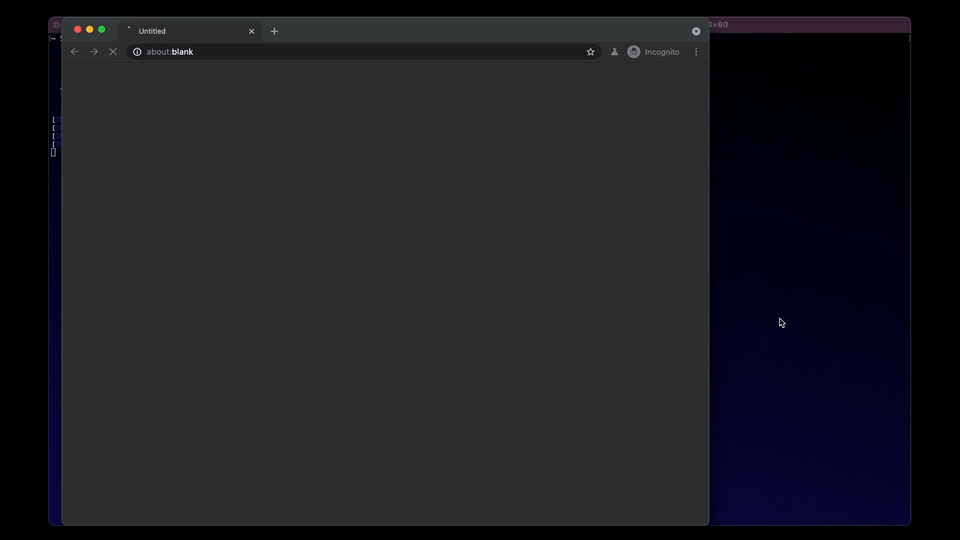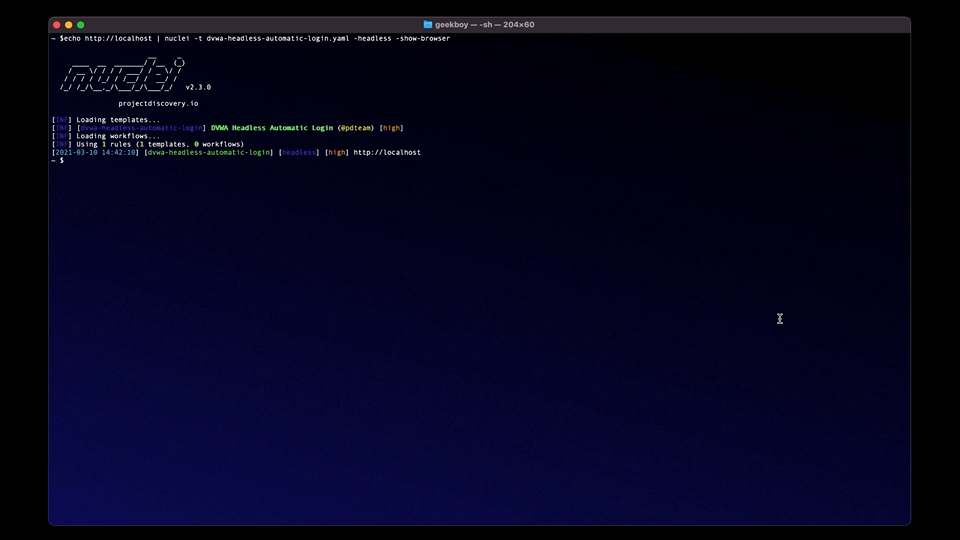
Headless mode works on the concept of actions, where each action manipulates the browser to do something. For example, navigating to a URL, clicking a button, running a script, etc. With these powerful primitives, users can automate almost all kinds of actions for headless.
As an example, the templates below detect DOM XSS in [window.name](http://window.name) source for 3 sinks - eval, document.write and innerHTML.
id: window-name-domxss
info:
name: window.name DOM XSS
author: pd-team
severity: medium
headless:
- steps:
- action: setheader
args:
part: response
key: Content-Security-Policy
value: "default-src * 'unsafe-inline' 'unsafe-eval' data: blob:;"
- action: script
args:
hook: true
code: |
!function(){function n(n){window.alerts.push(n)}function e(){var n;try{throw new Error("")}catch(e){n=e.stack||""}return(n=n.split("\n").map(function(n){return n.trim()})).splice("Error"==n[0]?2:1)}window.alerts=[],window.name="{{randstr_1}}'\"<>";var t=eval,r=(document.write,Object.getOwnPropertyDescriptor(Element.prototype,"innerHTML").set);Object.defineProperty(Element.prototype,"innerHTML",{set:function(t){return t.includes("{{randstr_1}}'\"<>")&&n({sink:"innerHTML",source:"window.name",code:t,stack:e()}),r.call(this,t)}}),eval=function(r){return r.includes("{{randstr_1}}'\"<>")&&n({sink:"eval",source:"window.name",code:r,stack:e()}),t.apply(this,arguments)},document.write=function(r){return r.includes("{{randstr_1}}'\"<>")&&n({sink:"document.write",source:"window.name",code:r,stack:e()}),t.apply(this,arguments)}}();
- args:
url: "{{BaseURL}}"
action: navigate
- action: waitload
- action: script
name: alerts
args:
code: "window.alerts"
matchers:
- type: word
part: alerts
words:
- "sink:"
extractors:
- type: kval
part: alerts
kval:
- alerts
Complete documentation for headless protocol is available at https://nuclei.projectdiscovery.io/templating-guide/protocols/headless/.
Some example templates for Headless Protocol are also provided at https://nuclei.projectdiscovery.io/template-examples/headless.
TCP Requests
Nuclei now allows users to model TCP-based protocols through the familiar YAML-based DSL. This allows Nuclei to act as a fully automatable netcat, sending raw data over network sockets and performing matching/extracting with chained flows on top of it. Helper functions are supported to allow users to encode and decode data in different formats. Precise matching is also allowed by reading bytes from the response in chunks and running different matchers on them.
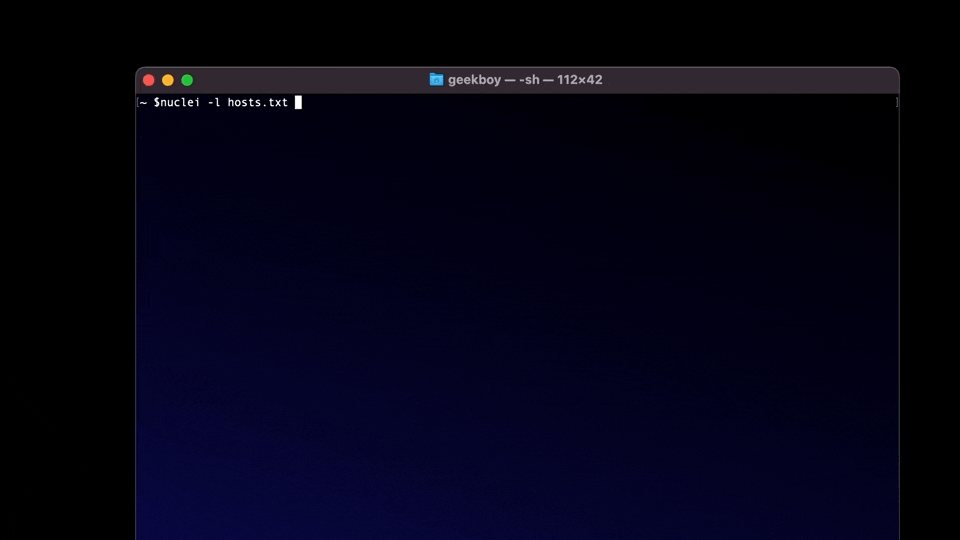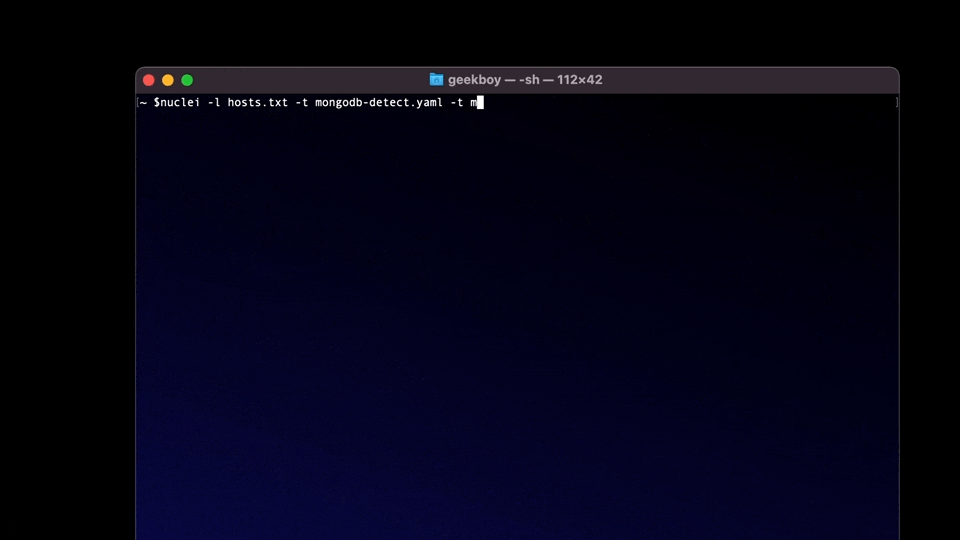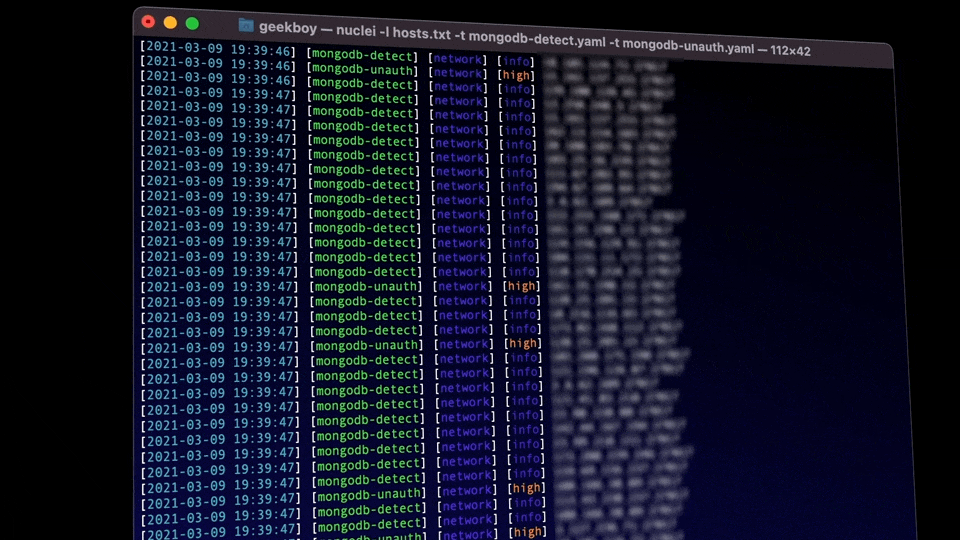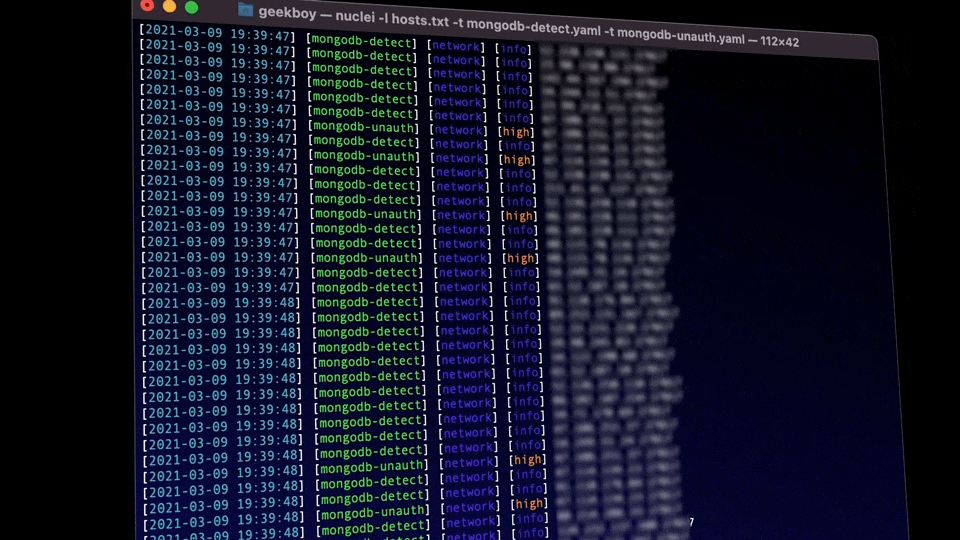
As an example, the template below detects an exposed Redis Server.
id: exposed-redis
info:
name: Redis Unauth Server
author: pd-team
severity: high
reference: https://redis.io/topics/security
network:
- inputs:
- data: "info\r\nquit\r\n"
host:
- "{{Hostname}}"
read-size: 2048
matchers-condition: and
matchers:
- type: word
words:
- "redis_version"
- type: word
negative: true
words:
- "redis_mode:sentinel"
Some example templates for Network Protocol are also provided at https://nuclei.projectdiscovery.io/template-examples/network/.
Complete documentation for network protocol is available at https://nuclei.projectdiscovery.io/templating-guide/protocols/network/.
File Requests
Files can now be processed by the nuclei engine with its matching and extracting capabilities. This allows users to write filesystem templates to detect misconfigurations/issues on the local system itself, making it a valuable tool for post-exploitation needs.
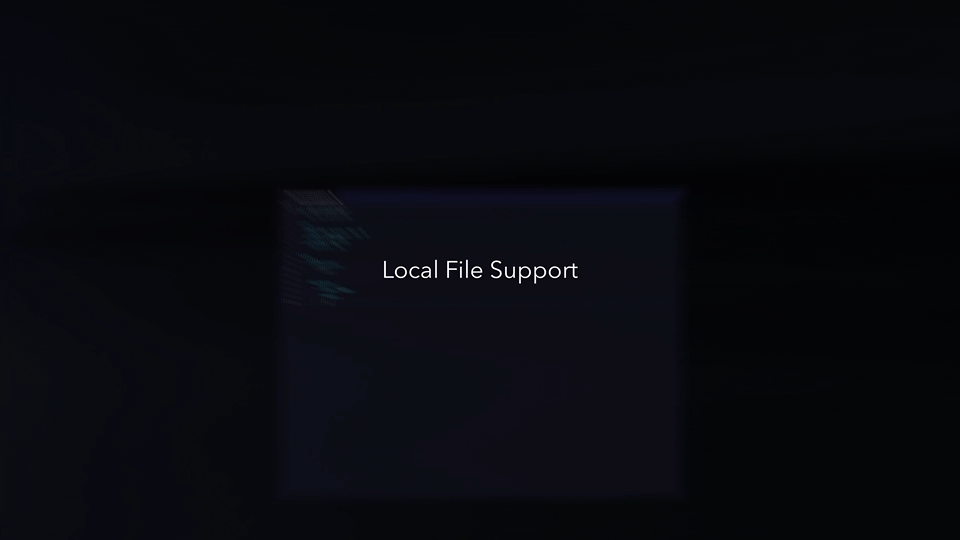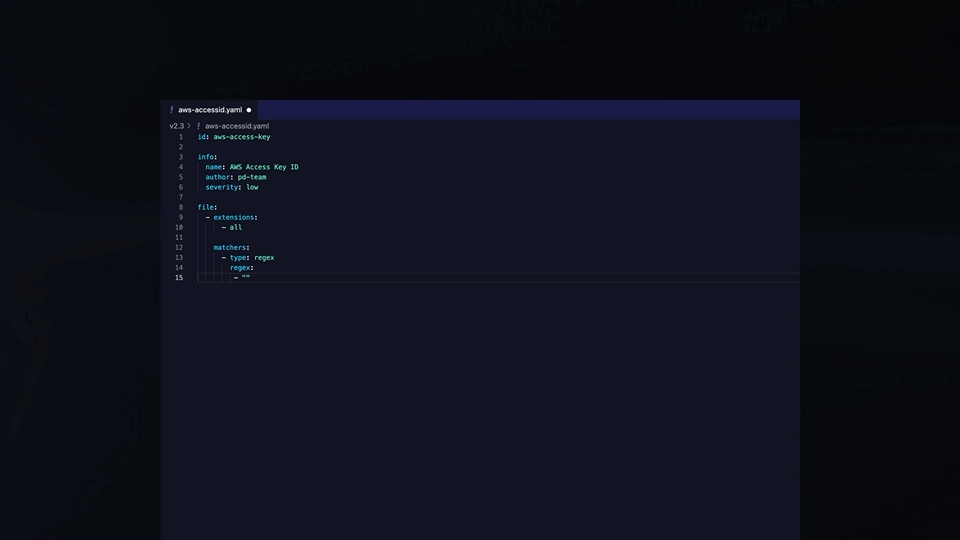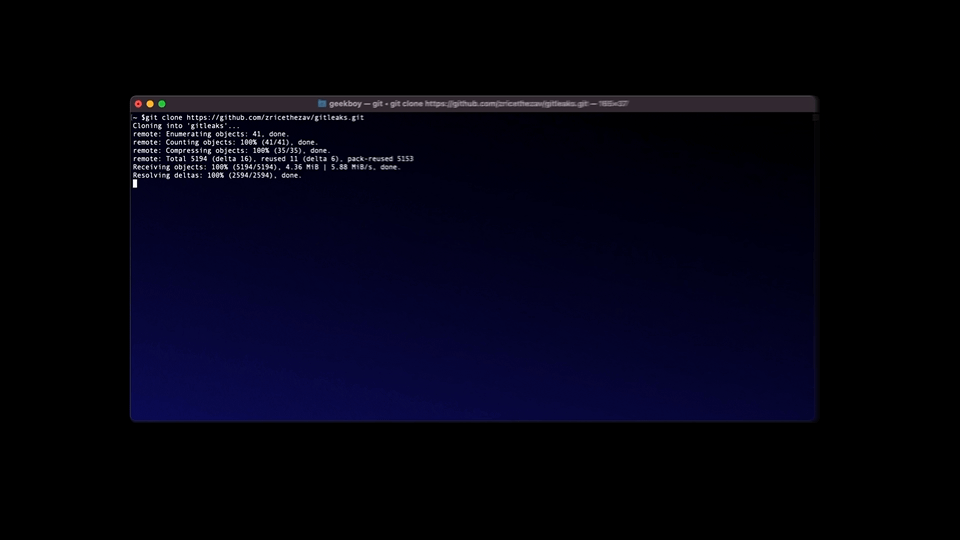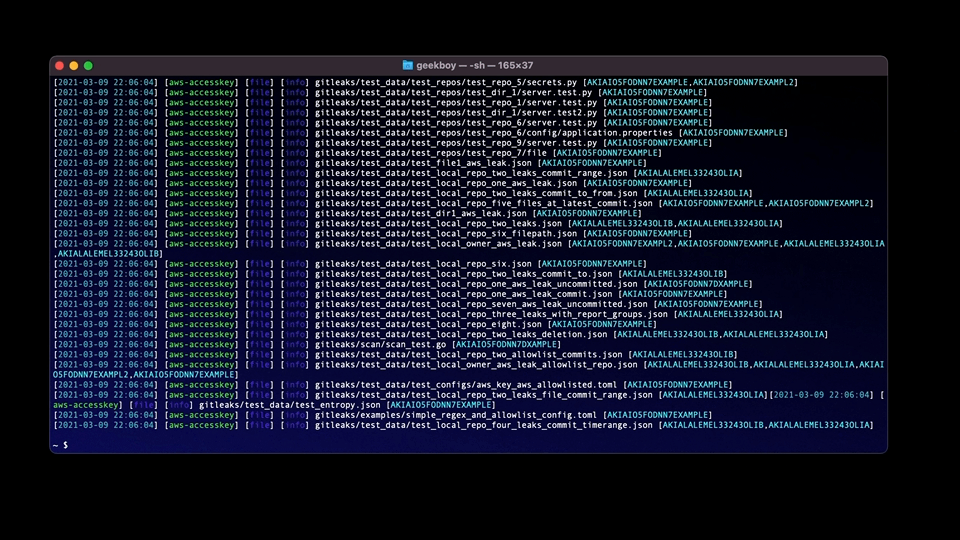
Complete control over extensions processed, and the data read is provided to the user. An example template to detect a Private Key is provided below.
id: private-key
info:
name: Private Key Detect
author: pd-team
severity: high
file:
- extensions:
- all
denylist:
- .pub
no-recursive: true
max-size: 1024 # read very small chunk
matchers:
- type: word
words:
- "BEGIN OPENSSH PRIVATE KEY"
- "BEGIN PRIVATE KEY"
- "BEGIN RSA PRIVATE KEY"
- "BEGIN DSA PRIVATE KEY"
- "BEGIN EC PRIVATE KEY"
- "BEGIN PGP PRIVATE KEY BLOCK"
- "ssh-rsa"
Complete documentation for file protocol is available at https://nuclei.projectdiscovery.io/templating-guide/protocols/file/.
Some example templates for File Protocol are also provided at https://nuclei.projectdiscovery.io/template-examples/file/.
Issue Tracker Integration
The new release comes with built-in integration with Issue Trackers like Jira, Github, and Gitlab with many more on the way. This allows direct importing of issues generated by Nuclei into issue trackers with automatic deduplication.

This makes running Nuclei into CI/CD job very convenient, with unique scan results added as issues with proper labels, assignees, etc., into an issue tracker of your choice.
All you require is a config file with details setup for your preferred issue tracker. An example config file -
allow-list:
severity: critical,high,medium
# jira contains configuration options for jira issue tracker
jira:
# URL is the jira application url
url: "https://test.atlassian.net"
# account-id is the account-id of the jira user
account-id: "xxxxxxxxxxxxxxx"
# email is the email of the user for jira instance
email: "test@test.com"
# token is the token for jira instance.
token: "xxxxxxxxxxxx"
# project-name is the name of the project.
project-name: "XXXX"
# issue-type is the name of the created issue type
issue-type: "Bug"
Running the following command will automatically run Nuclei with issue tracker reporting enabled and issues found will be sent to the server.
./nuclei -t <template> -l <input> -report-config <issue-tracker-config>.yaml
Tag Based Execution Support
Tag-based execution support has been added to Nuclei, allowing comma-separated tags to be added that uniquely identify a template. Users can then run templates without specifying their absolute paths, providing only tags.
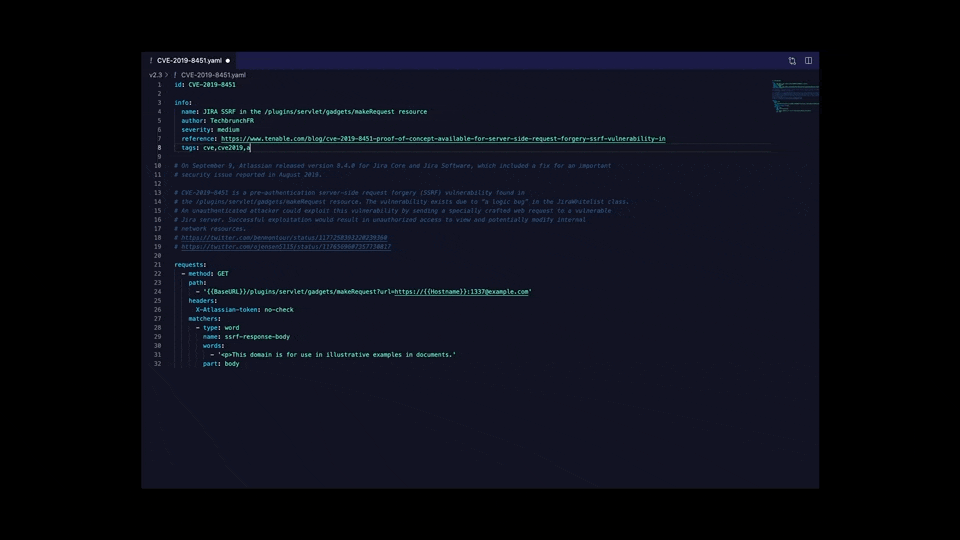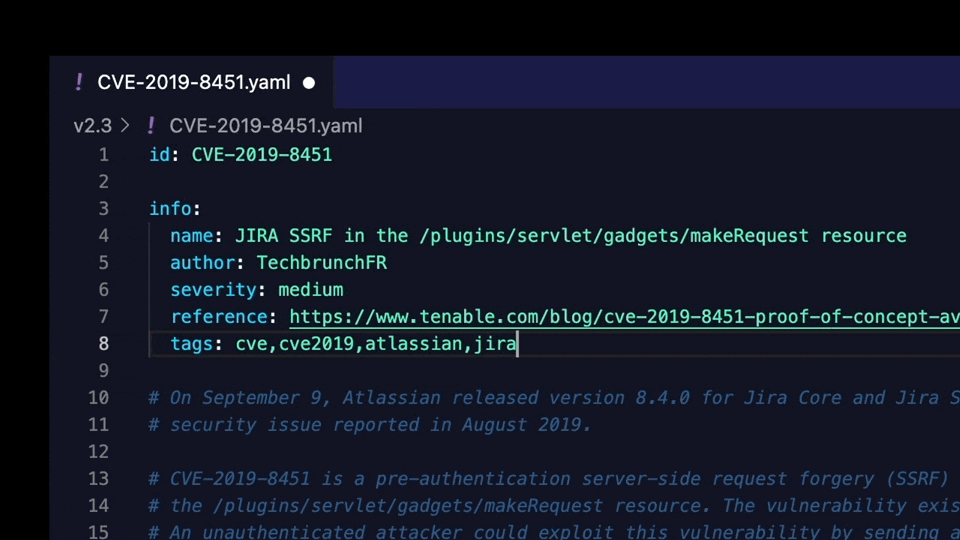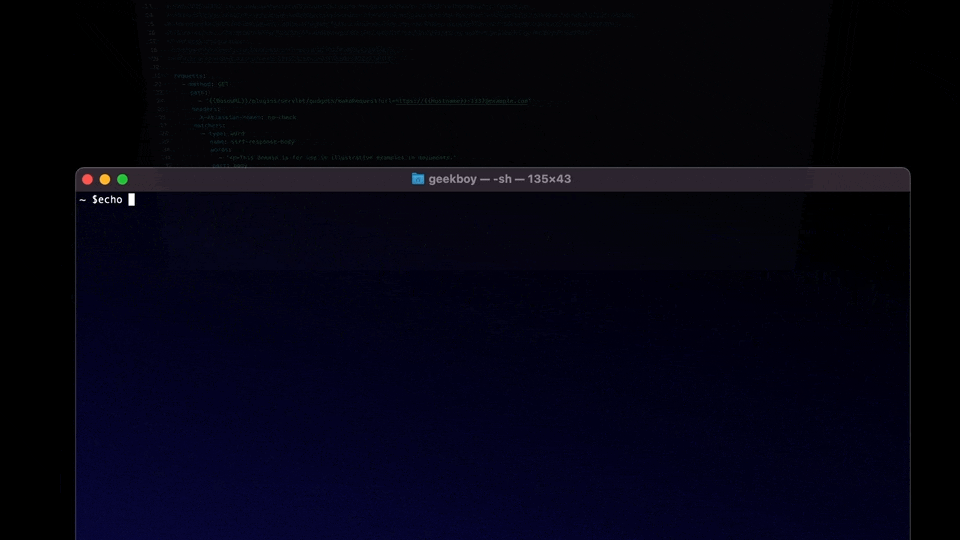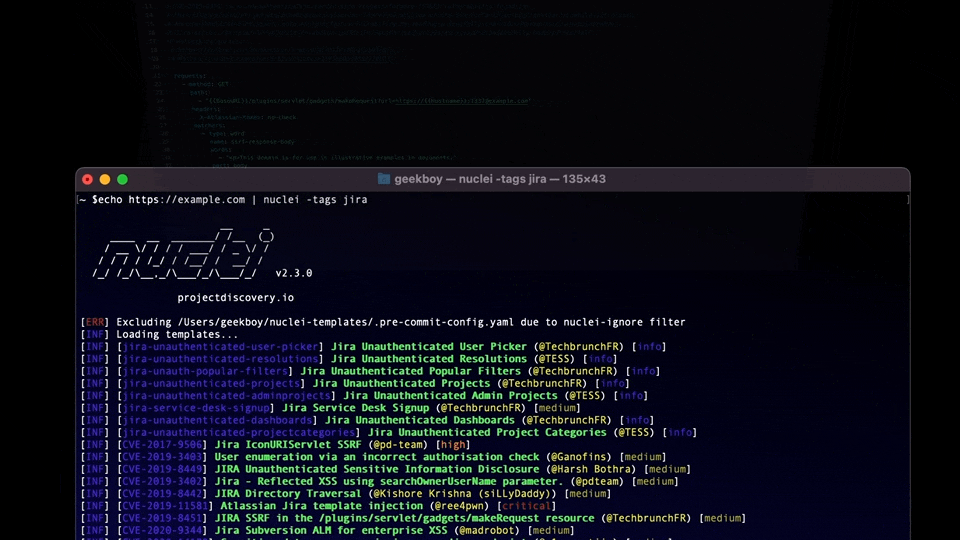
An example template with tags in its info block:
id: CVE-2019-15043
info:
author: bing0o
name: Grafana unauthenticated API
severity: medium
tags: cve,cve2019,grafana
The tags to run can be specified on the Nuclei command line as provided below:
./nuclei -tags cve -l urls.txt
./nuclei -tags cve2021 -l urls.txt
./nuclei -tags logs,backups -l urls.txt
./nuclei -tags lfi,rce -l urls.txt
Config File Support
Configuration file support has been added to Nuclei, allowing you to continue using your various Nuclei configurations for different projects.
A default global configuration file is written in $HOME/.config/nuclei/config.yaml and is always read by Nuclei. It can be used to define your global configurations, such as any custom HTTP headers, rate limits, etc.
Ideally, the user should create a separate copy of the configuration file with options tailored to that project. So, if the target requires you to send a custom header, you can add that header to the configuration file for that project, and it will always be sent to the target when running Nuclei with the mentioned configuration file.
Miscellaneous Changes
- The workflow engine has been reworked, removing the Tengo Scripting layer. This makes workflows simpler and faster, and also safer, by removing the need to sandbox the execution of workflows.
- Nuclei can now cluster identical HTTP Requests (previously limited to GET requests) in templates provided by the user, instead of making a new request each time. This reduces the scan time and also noise-generated by the scan.
- Passive HTTP Support has been added. This allows available Nuclei HTTP templates (limited to templates for root paths) to be run on the passively collected data (from tools like httpx, meg, etc) and perform post-processing on them! This feature is available with
-passiveflag in Nuclei.
What's next for Nuclei?
This release has been a big one, with lots of stuff being added. Moving ahead, with more stable architecture, we'll be working towards adding more features and other additions that optimize the scanning process.
We'll add more templates for these newly added protocols and work on more blog posts for these new features. We'll also add support for more protocols/features with the upcoming releases. A list of planned features is given below:
- Interact.sh Integration - Discover OOB bugs that cannot be detected by normal fuzzing. Catch remote interactions with built-in request correlation and matching for OOB payloads.
- More network protocols support - Support for protocols such as SSH, SMB, etc. will be added to Nuclei allowing more templates to be written for network security needs.
- Nuclei Live - A graphical builder for simplifying the template creation process.