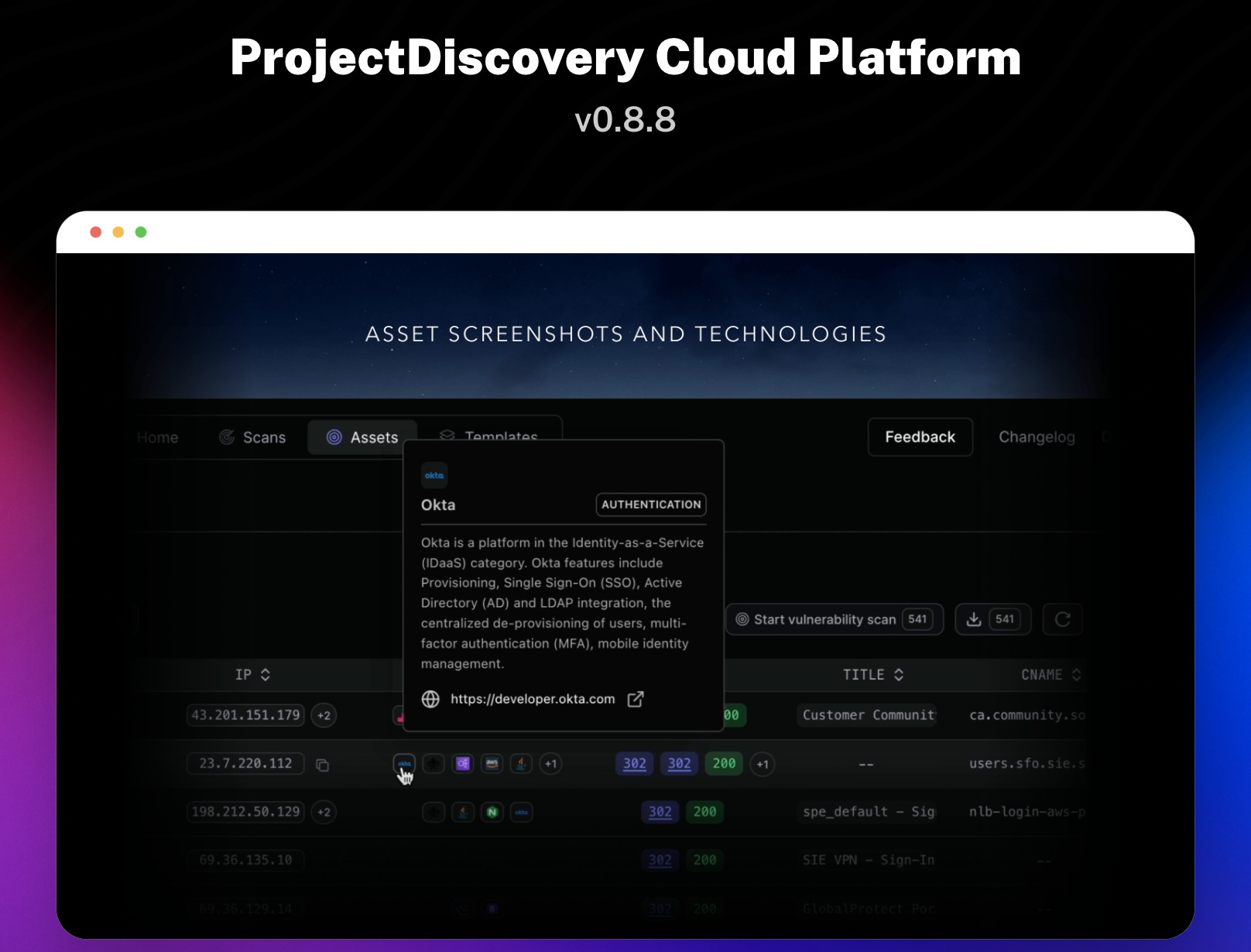
Interactsh v1.0.0 brings more stability, new protocols support, and a slew of other improvements and security fixes.
Server Pool Support + random selection
With new vulnerabilities being released recently which relied on DNS interactions (log4j), interactsh servers started receiving lot more load from nuclei scans than they could withstand.
With the new interactsh release, the client has been modified to support a list of interactsh servers from which a server is randomly selected for use. This eliminates the single point of failure and distributes the load among a dynamic pool of servers. Interactsh client now use following list of default interactsh server to use:
- oast.pro
- oast.live
- oast.site
- oast.online
- oast.fun
- oast.me
LDAP Server support
Another thing that was added to the interactsh server after the Log4j vulnerability was an LDAP server as the vulnerability detection relied on communication with an LDAP server.
Canary-based interaction for LDAP protocol is currently only supported for Search requests which is the commonly used method. Full logging can also be obtained for LDAP protocol with a self-hosted interactsh server by using ldap flag.
FTP Server Support
Support for capturing FTP based interactions has also been added for self-hosted interactsh servers.
ACME TLS Improvements
Previous versions of interactsh server relied on an unmaintained ACME library which was causing issues on some setups.
The ACME implementation has been changed to use the excellent Certmagic library from Caddy. This makes the ACME process more stable and fault-tolerant as the library is very battle-tested.
A few bugs in the ACME registration process were also identified and fixed during this change.
Bug-fixes & Changes
It was identified that under very heavy load, the caching library used by interactsh-server for storing interactions was becoming unresponsive and got stuck on reads/writes. This was mitigated by switching to goburrow/cache which provides much better performance and numbers for same workload.
Multiple bugs were fixed in the DNS server component of the interactsh-server. The handling of Unique ID in DNS questions was fixed to support case insensitive values. The NS questions handling was fixed to included response in Answer section which fixed a bug with NS question resolving.
Security Fixes
A subdomain takeover was reported in the interact-server component by Melih at our security@projectdiscovery.io. The bug was related to a CNAME entry in the DNS server which was earlier used to host the interactsh web client.
The bug was fixed in the latest release by removing the DNS entry, please read the GitHub advisory for more information.