Update: PD-Actions GitHub project is suspended by GitHub team due to abuse of Actions platform by malicious actors using PD-Actions.
"GitHub Actions help you automate tasks within your software development life cycle. GitHub Actions are event-driven, meaning that you can run a series of commands after a specified event has occurred. For example, every time someone creates a pull request for a repository, you can automatically run a command that executes a software testing script."
What this means to us?
GitHub lets us run our projects on their cloud in a programmatic manner using GitHub action workflows. Github also lets us schedule these runs and offers free 2000 minutes/month for all Github users.
At ProjectDiscovery, we automated many tasks using GitHub Actions to reduce manual work. These tasks include release build automation across all FOSS projects, Github pages deployment for the blog, BugBounty change index at chaos website, and so on.
Example of a Github Actions utilising workflows (workflows are defined using the YAML configuration file under .github/workflows/ directory):
jobs:
job1:
runs-on: ubuntu-latest
# Map a step output to a job output
outputs:
output1: ${{ steps.step1.outputs.test }}
output2: ${{ steps.step2.outputs.test }}
steps:
- id: step1
run: echo "::set-output name=test::hello"
- id: step2
run: echo "::set-output name=test::world"GitHub Actions for Application Security
Github Actions can be utilized to execute a series of security steps to automate manual tasks. In this blog post, we are going to take a look at how we can use Github Actions to perform a continuous asset discovery and vulnerability assessment using a set of tools we have open-sourced.
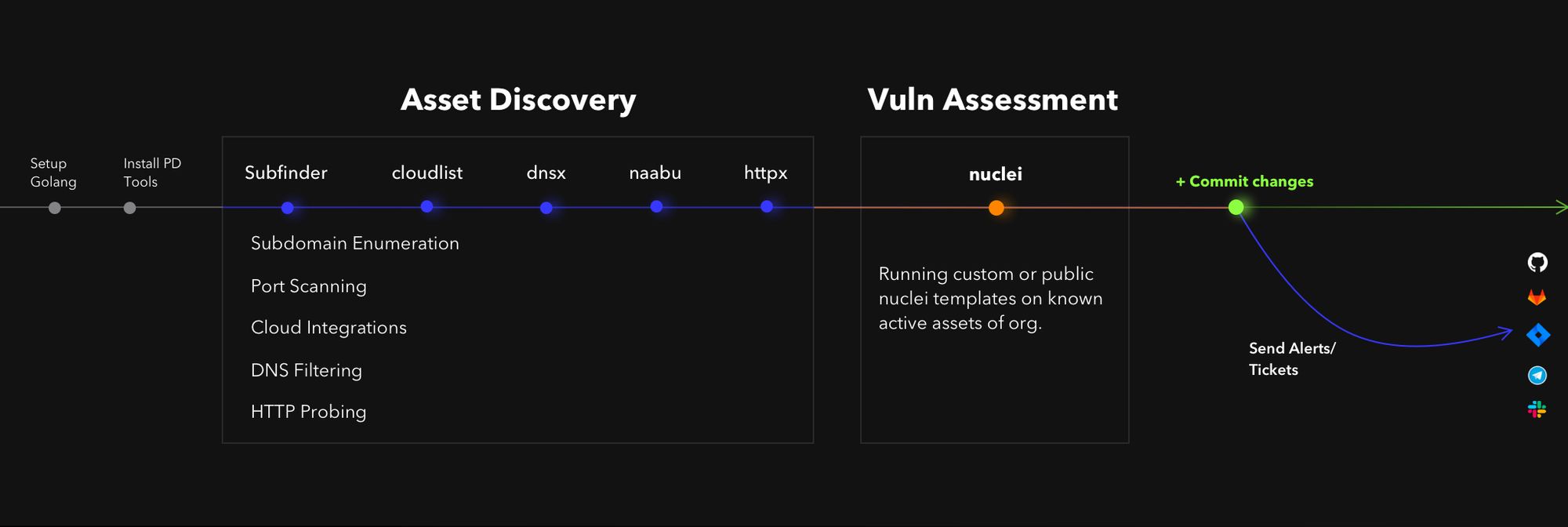
We have crafted a workflows PD-Actions utilizing our tools to perform a continuous asset discovery and vulnerability assessment. We have included all the details in the Github README to set up and run PD-Actions with your Github account, similarly, you can define your own workflows to perform various kinds of security assessments.
Breakdown of PD-Actions workflow
Workflow name definition
name: pd-actions
Defining ON events
on:
schedule:
- cron: '0 0 * * *'
workflow_dispatch:
Defining Jobs and Steps
Build definition
jobs:
build:
runs-on: ubuntu-latest
Checkout repo
- name: Checkout Repo
uses: actions/checkout@master
Setting up Golang
- name: Setup golang
uses: actions/setup-go@v2
with:
go-version: 1.14
Installing ProjectDiscovery tools
- name: Setting up ProjectDiscovery tools
run: |
GO111MODULE=on go get -v github.com/projectdiscovery/subfinder/v2/cmd/subfinder
GO111MODULE=on go get -v github.com/projectdiscovery/dnsx/cmd/dnsx
sudo apt-get install libpcap-dev # Required for Naabu
GO111MODULE=on go get -v github.com/projectdiscovery/naabu/v2/cmd/naabu
GO111MODULE=on go get -v github.com/projectdiscovery/httpx/cmd/httpx
GO111MODULE=on go get -v github.com/projectdiscovery/nuclei/v2/cmd/nuclei
shell: bash
Running ProjectDiscovery tools
- name: Running SubFinder for passive DNS enumeration
run: |
subfinder -dL input/domains.txt -config config/subfinder-config.yaml -o output/passive_subdomains.txt
shell: bash
- name: Running dnsx for valid DNS filtering
run: |
dnsx -l output/passive_subdomains.txt -t 50 | tee output/active_subdomains.txt
shell: bash
- name: Running naabu to check top 100 ports
run: |
naabu -iL output/active_subdomains.txt -rate 10000 -top-ports 100 | tee output/active_ports.txt
shell: bash
- name: Running httpx for HTTP webservers probbing
run: |
httpx -l output/active_ports.txt | tee output/active_urls.txt
shell: bash
- name: Downloading Nuclei Templates
run: |
nuclei -update-templates
shell: bash
- name: Running Nuclei for vulnerability assessment
run: |
nuclei -t cves/ -l output/active_urls.txt -bs 100 -c 50 -rl 300 -nc | tee output/nuclei_output.txt
shell: bash
Sorting the results
- name: Sorting the output results
run: |
find output -type f -exec sort {} -o {} \;
shell: bash
Create local changes
- name: Create local changes
run: |
git add output/passive_subdomains.txt
git add output/active_subdomains.txt
git add output/active_ports.txt
git add output/active_urls.txt
git add output/nuclei_output.txt
Committing results to GitHub
- name: Commit results to GitHub
run: |
git config --local user.email "sandeep@projectdiscovery.io"
git config --global user.name "projectdiscovery"
git commit -m "PD-Actions report" -a --allow-empty
Push changes to GitHub
- name: Push changes
uses: ad-m/github-push-action@master
with:
github_token: ${{ secrets.GITHUB_TOKEN }}
branch: ${{ github.ref }}
Who can use PD-Actions?
With the simplicity of the Github Actions, you can create all sorts of automation for your different security workflows. Even with the given repository,
Security Engineers — perform continuous asset discovery and vulnerability assessment of your organization. You can also utilize Cloudlist (e.g. to pull assets from Route53), and test for any vulnerabilities on pre-production apps.
Pen-testers / Bug bounty hunters - if you're actively testing any programs/scope, PD Actions could help in minimising many steps needed in preliminary recon and vulnerability assessment. If you're a bug hunter, it is always best to customise your assessment steps using your own Nuclei-templates. It is very easy to get started, and develop your own template. PD-Action will handle all your tasks actively and even create an issue whenever a vulnerability is detected.
Takeaways
GitHub Actions is awesome. You can run your security automations on the cloud without any additional setup. You can also use it for free for most of your jobs. Explore Github Actions here, and automate your frequent manual steps.
Got some questions? Feel free to jump in our discord server to discuss more Github Actions, security, and automation.