We are excited to announce the release of Nuclei v2.8.0 with new fuzzing capabilities, shared variables for workflows, GitHub/AWS S3 template downloads, integration with asnmap, uncover, and httpx, and of course much more!
These are just a few highlights from the 30+ improvements in this release. Read on to check out all of the significant updates.
We also want to thank the ProjectDiscovery community for the 5+ contributions they provided to Nuclei v2.8.0! At ProjectDiscovery, the community is the core; we could not be more proud of our community and team. We hope you enjoy the new release. Happy hacking!
Key additions in Nuclei v2.8.0
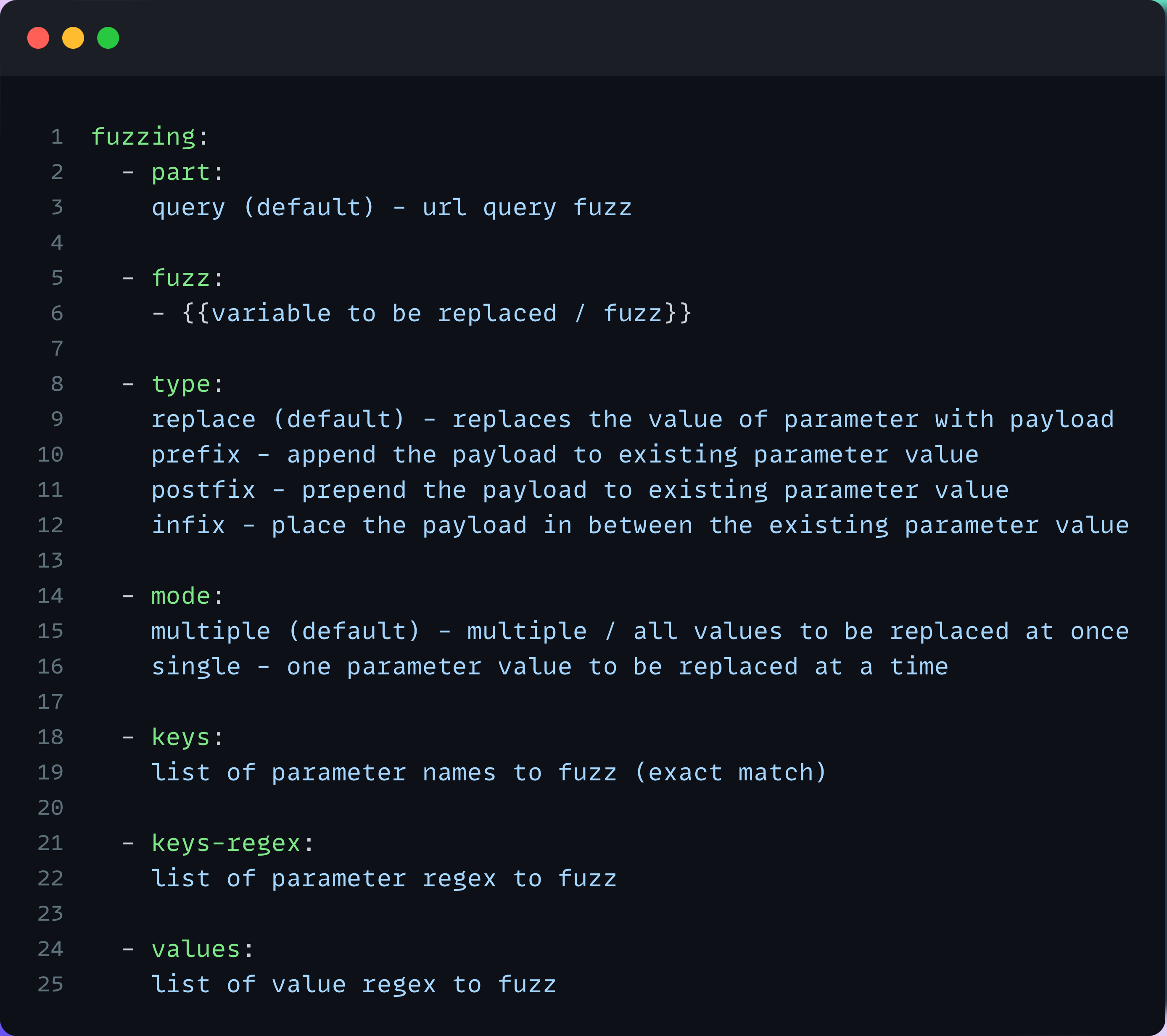
URL Fuzzing
Imagine a fast and customizable vulnerability scanner based on simple YAML-based DSL instrumented with integrated powerful fuzzing capabilities. Now stop dreaming– it's Nuclei!
Until now, fuzzing has been limited to pre-defined URLs, where one can define the paths or parameters to be fuzzed. This new feature allows Nuclei to fuzz arbitrary query parameters with a set of pre-defined payloads. And, of course, with the new feature are a lot of new possibilities: you can now fuzz to find well-known security vulnerabilities such as redirects, XSS, SSRF, RCE, SQLi, and more.
The new fuzzing feature currently only supports query parameters, but it will be expanded to include header/body and response in the future release. It offers complete replacement as a default option and positional interpolation on single or multiple query parameters. Many more capabilities are on the way. See the option details below for more information.
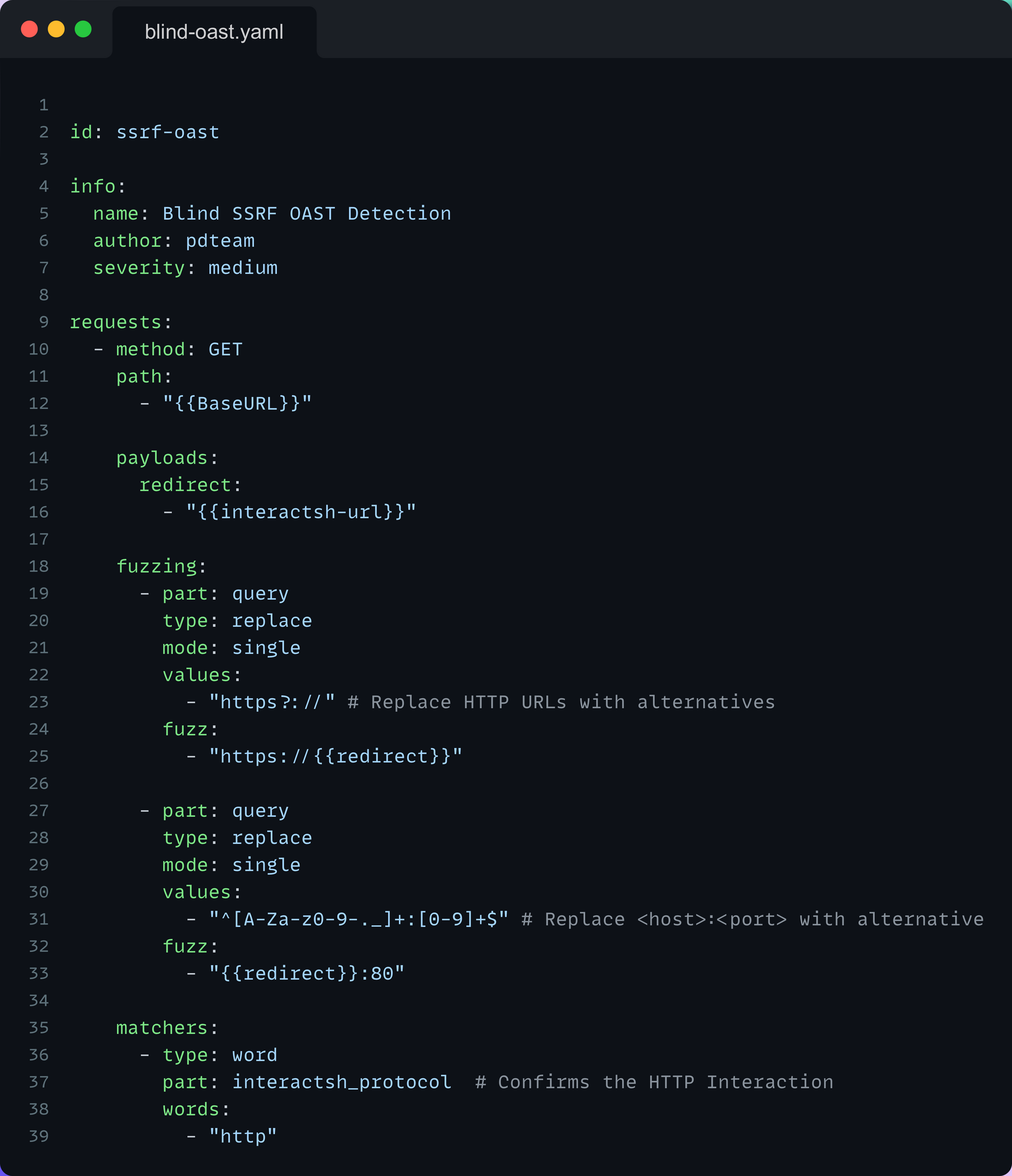
Here is a minimal template example for query parameter fuzzing:
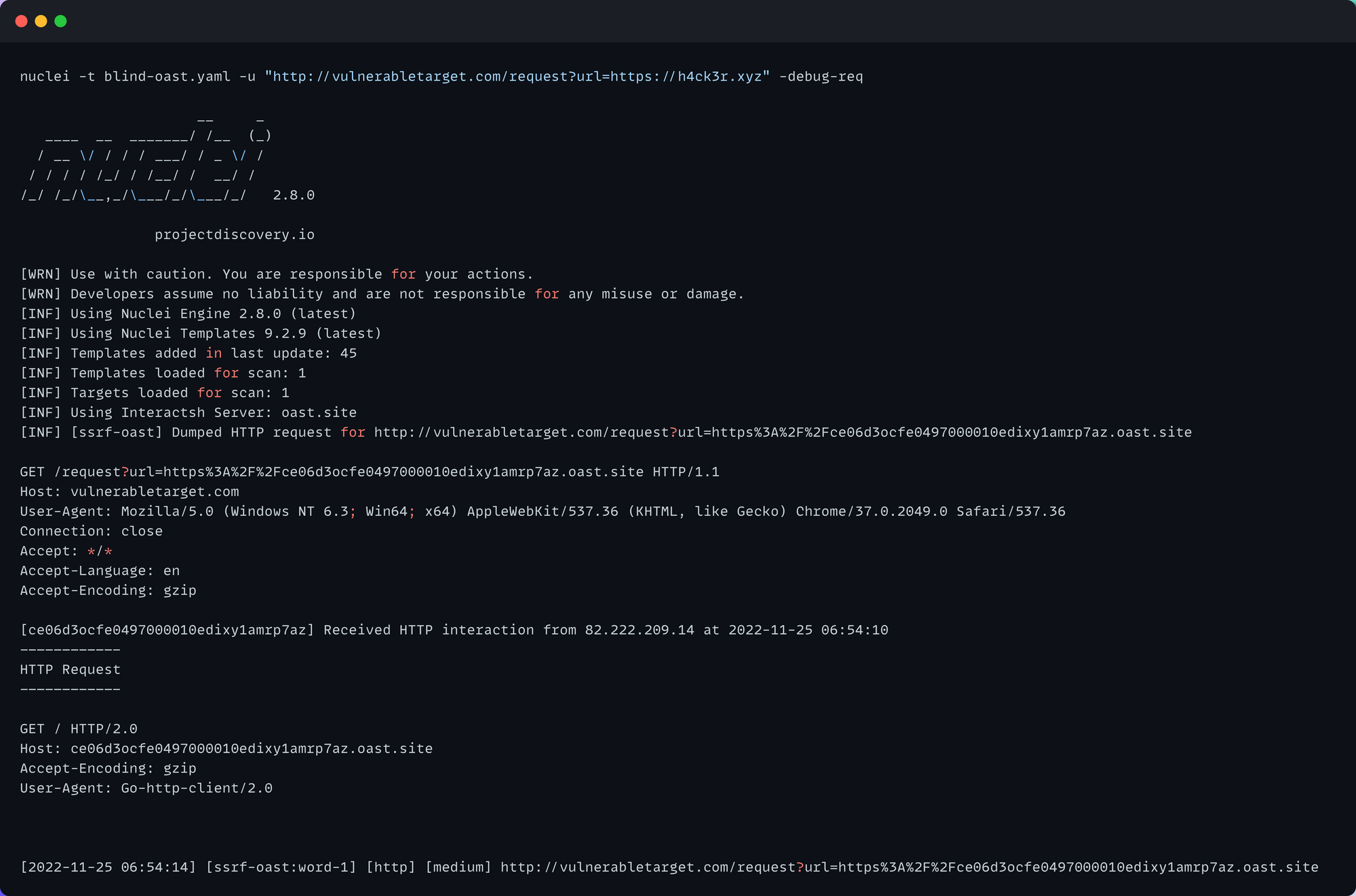
Looking for a way to uncover unknown security vulnerabilities in parameterized URLs? Check out the fuzzing-templates repository, where we've compiled a list of example templates you can use for this purpose. These templates are a great starting point for your own fuzzing efforts, so take a look and see how they can help you improve the security of your applications.
We are committed to continually expanding this project with new fuzzing templates, and we welcome contributions from community members. If you have ideas for templates that would help increase the coverage of the project, please share them with us. Your contributions will help make this project even better.
Separate template repository, why?
Fuzzing improves security testing and uncovers bugs that mortal eyes would have often missed. But its thorough approach requires significant execution time. Thus, testing fuzzing templates against targets in Nuclei by default would increase the scanning time. No one would want to wait for sooooo long! Unless fuzzing is what you want. We didn't want that either. We wanted this to be optional. That's why we are starting with a completely separate repository for the fuzzing templates.
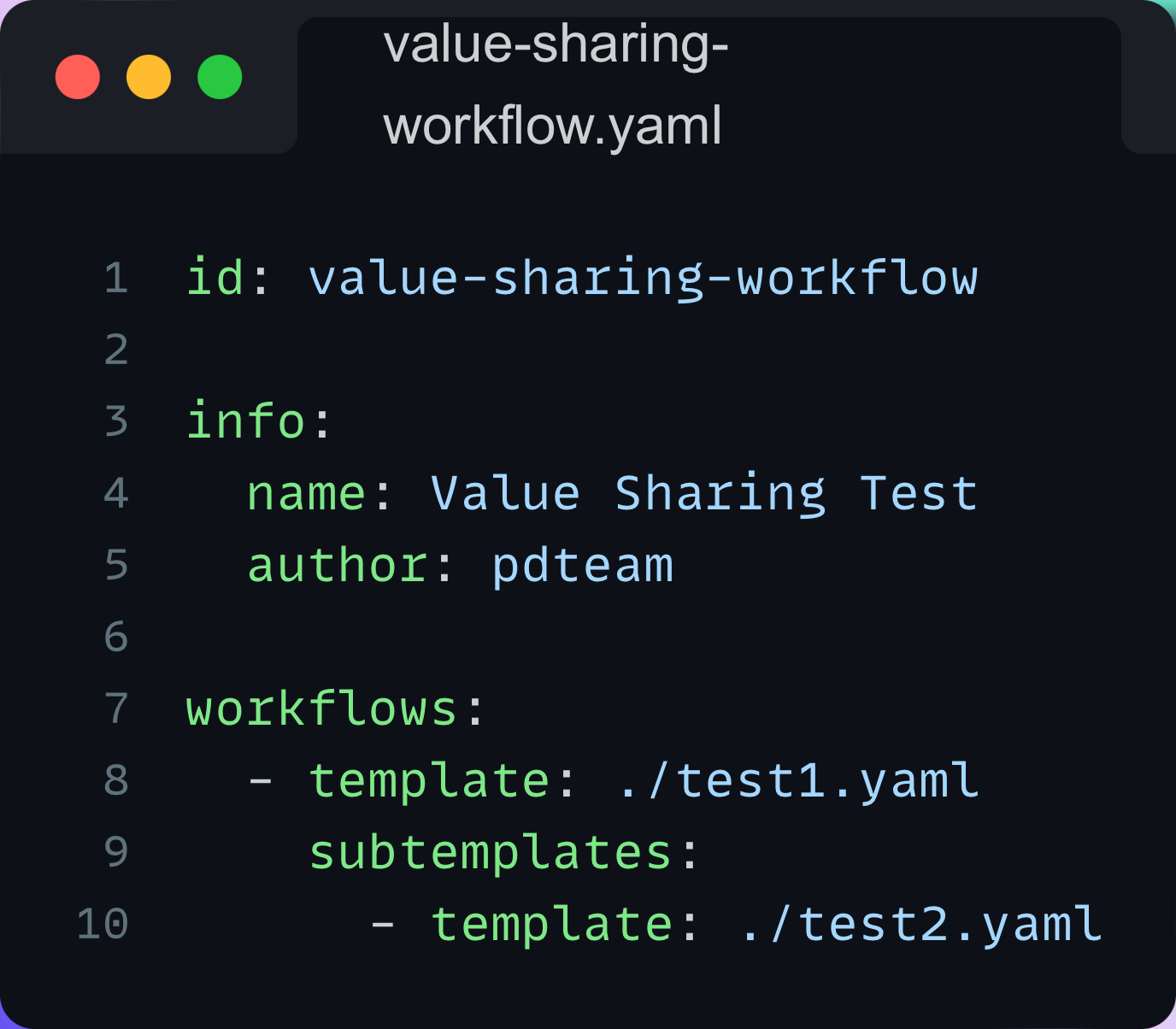
Shared Session/Values Between Templates
In Nuclei v2.8.0, We are introducing a new workflow feature, i.e., Shared execution context between templates. This means that all templates in the same workflow will have access to the same information, such as named extractors and session data. This allows templates to share and use the same data, making your workflow more efficient and effective.
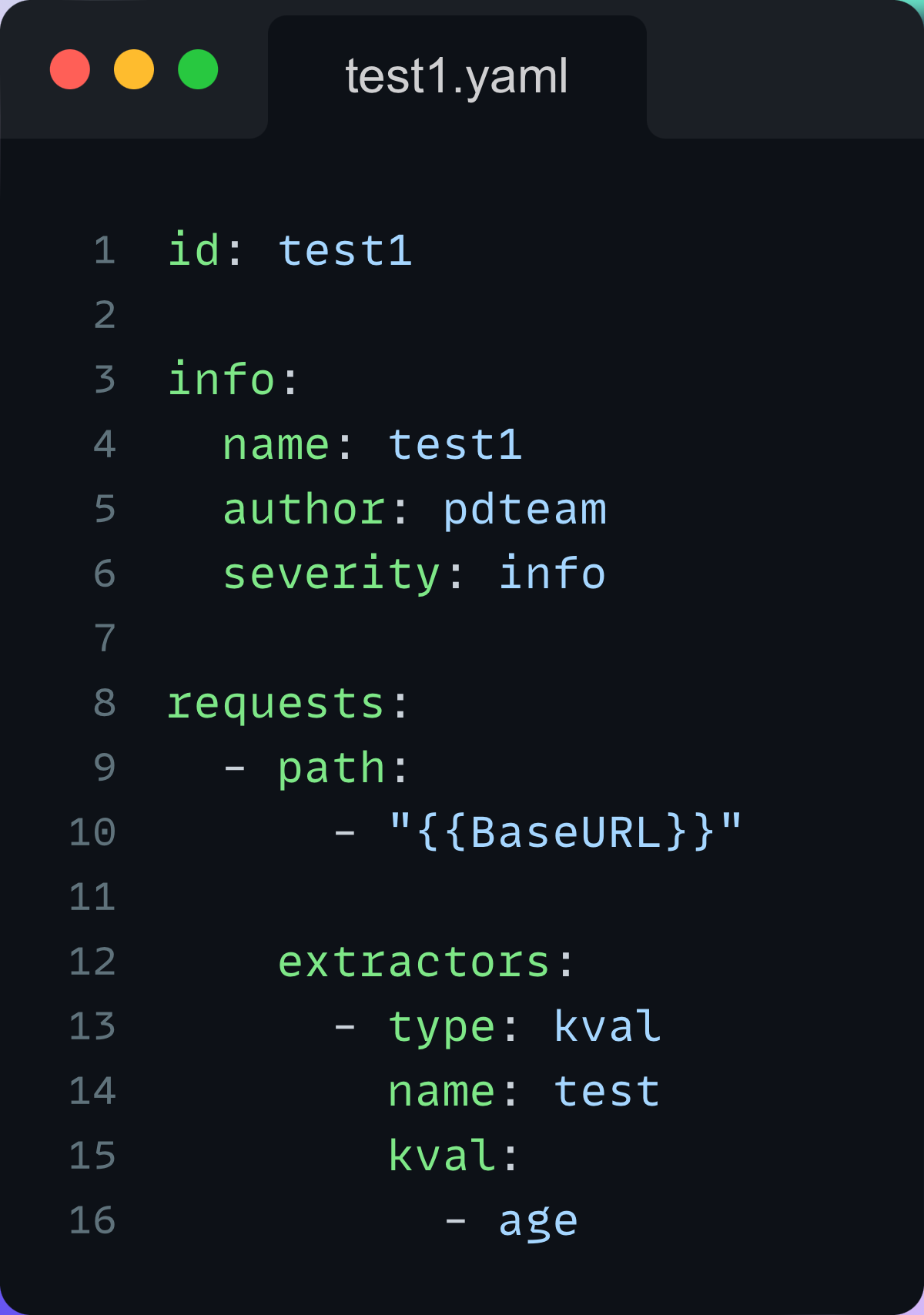
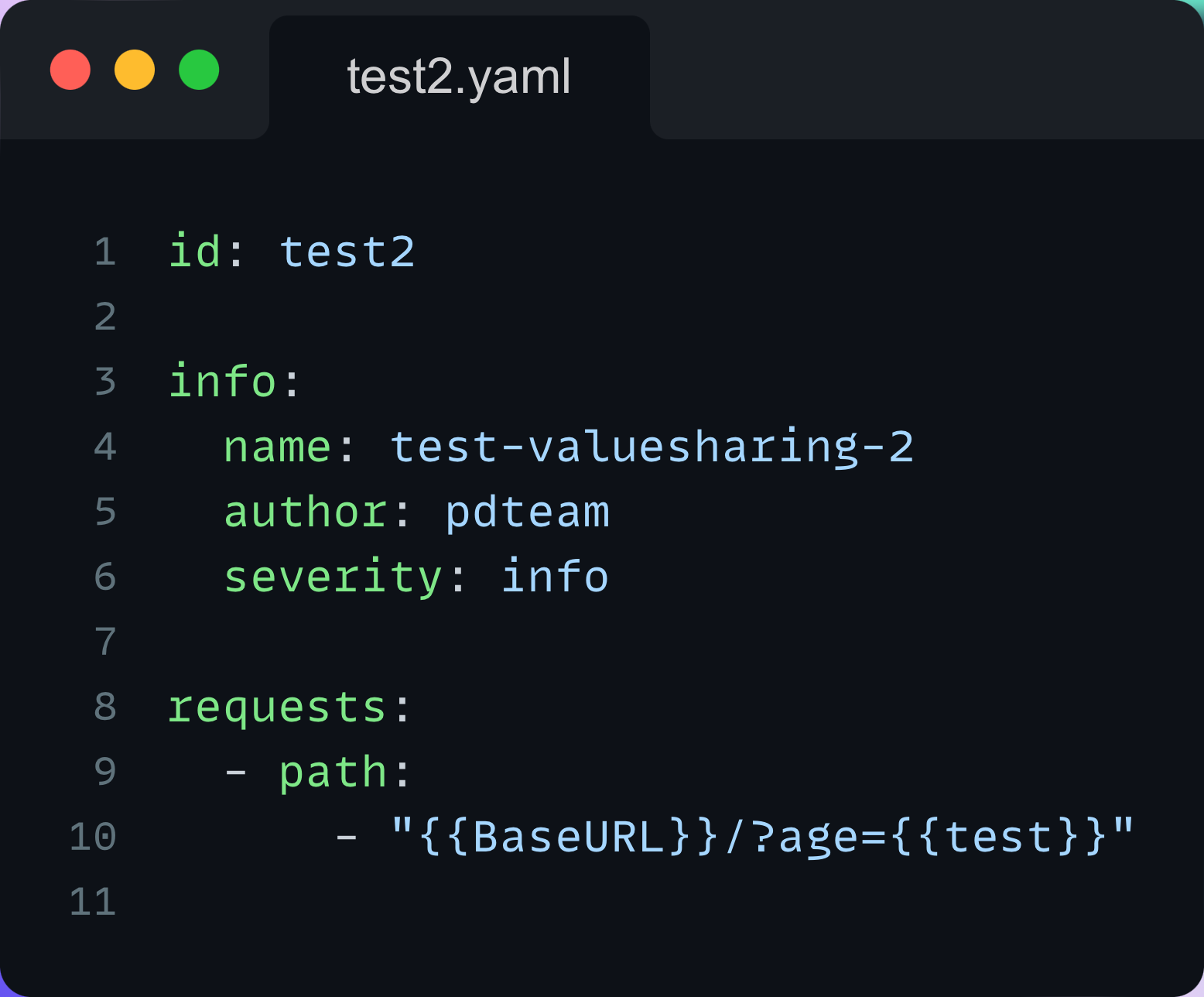
Here is an example of a workflow that extracts a value from the first template and uses it in the second one:
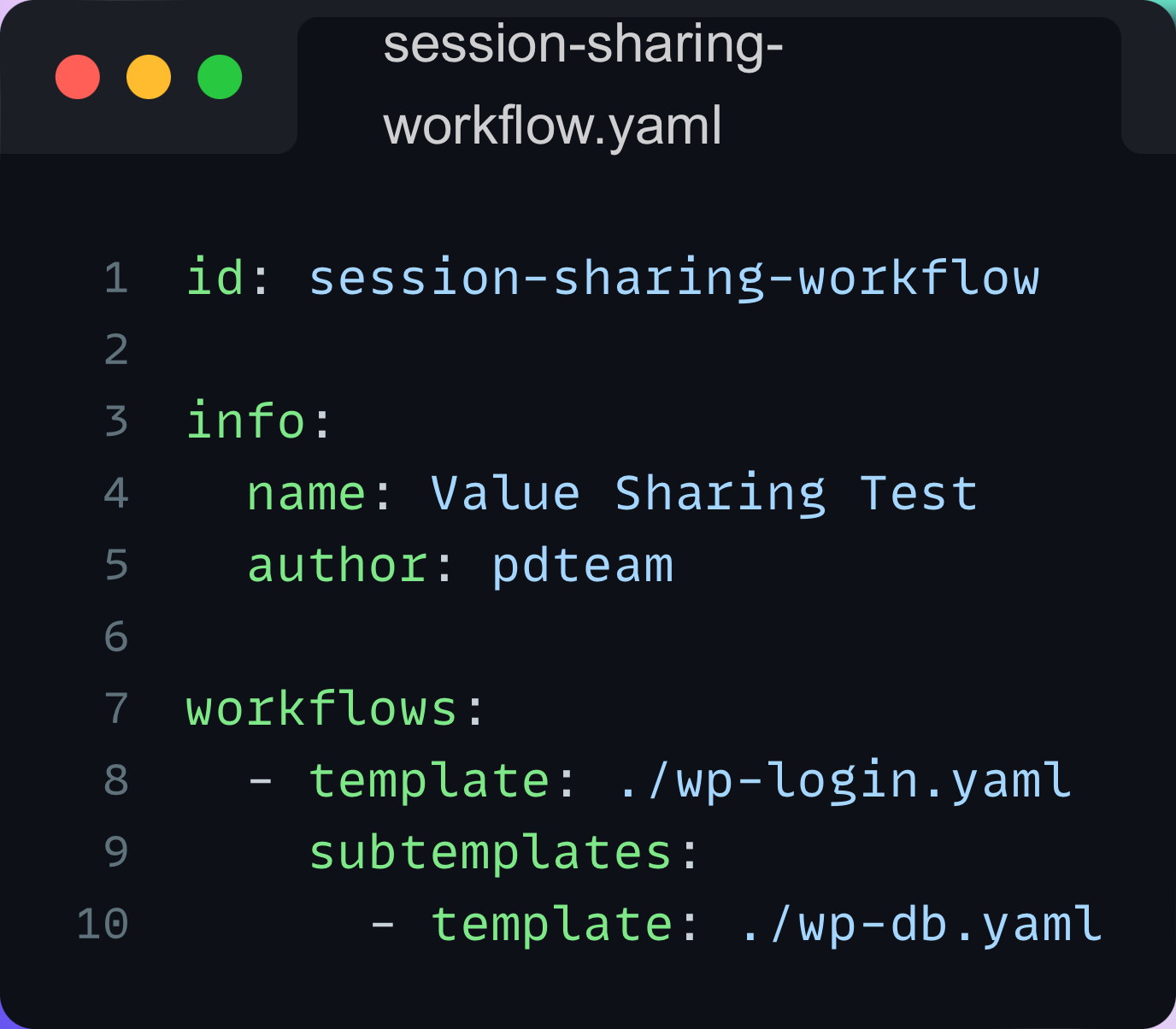
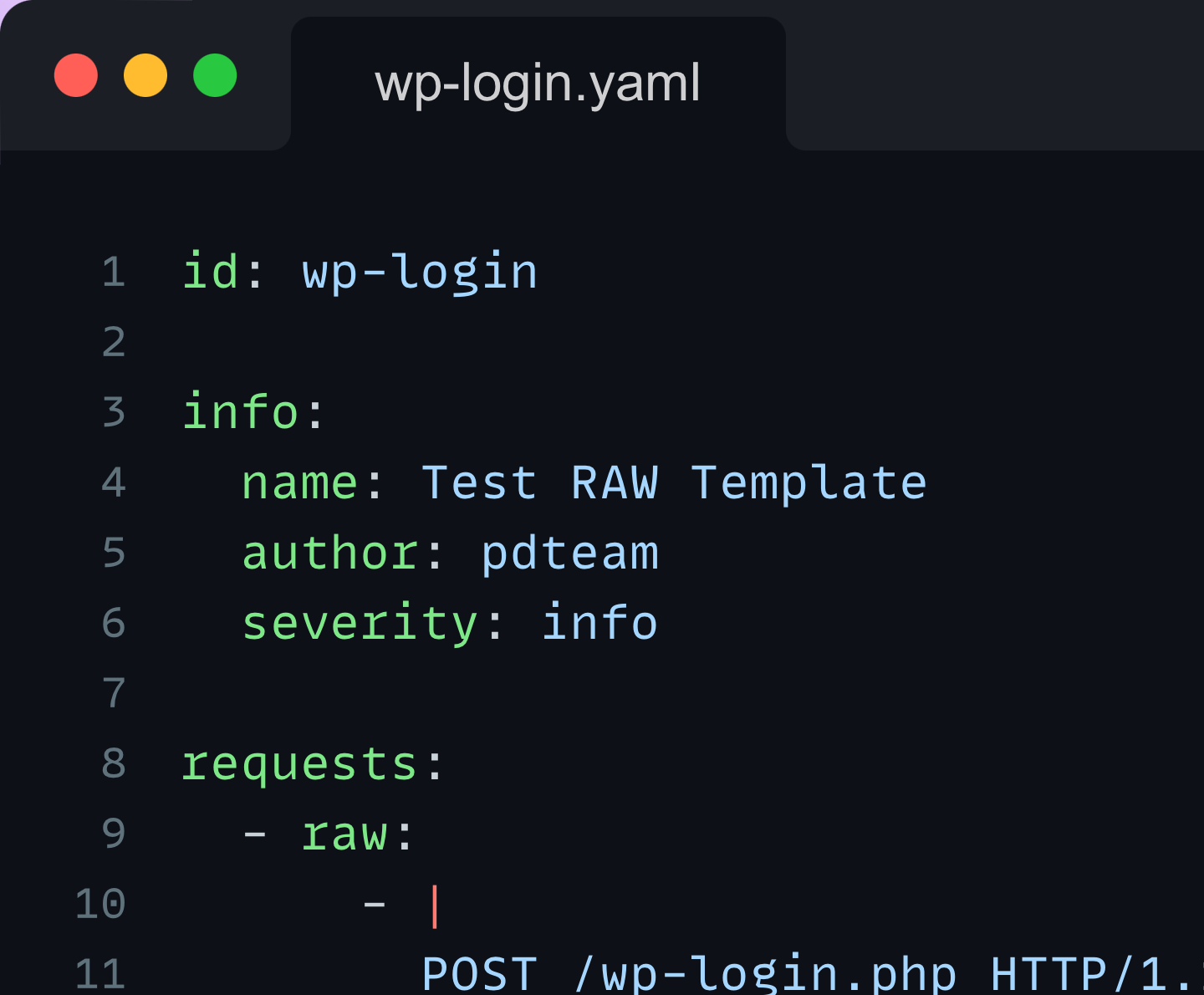
And, another example of a workflow that shares a session from the first template and uses it in the second one:
Integrations
We are always trying to build a better experience for the community. In Nuclei v2.8.0, we are adding integrations with other ProjectDiscovery tools!
This improvement means no more pipelining/chaining of commands to get inputs to Nuclei--several tools (and more to come) can be directly called when running the nuclei command.
ASNMap Integration
What are ASNs?
An Autonomous System (AS) is one or more IP prefixes, typically run by one network operator, with a clearly defined routing policy. An Autonomous System Number (ASN) is the identifier for that Autonomous System.
Many large organizations have their own ASN. ASNs are extremely useful for reconnaissance because they allow us to enumerate IP prefixes owned by that organization.
What is ASNMap?
ASNmap is another ProjectDiscovery tool, written in Golang, used to query Autonomous System data. The data is pulled from https://api.asnmap.sh, which returns data that is parsed from Frank Denis' legendary IPtoASN database.
Put simply, ASNMap converts:
- Organization names to CIDR ranges
- ASN numbers to CIDR ranges
- IP addresses to CIDR ranges
- Domain names to CIDR ranges
The results can be viewed in JSON, CSV, and text formats, so it's easy to pipe the output into other tools. To Nuclei, for example.
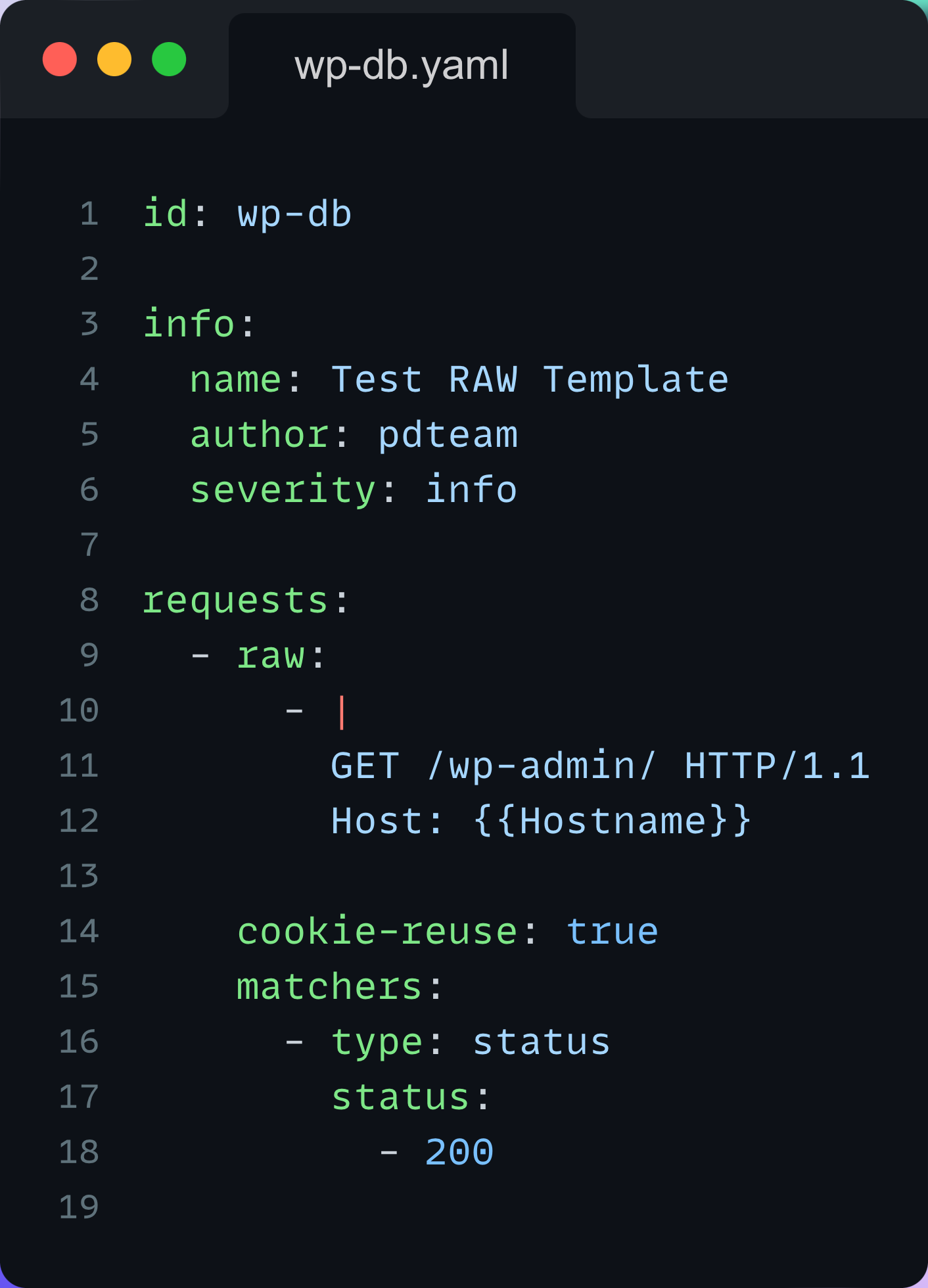
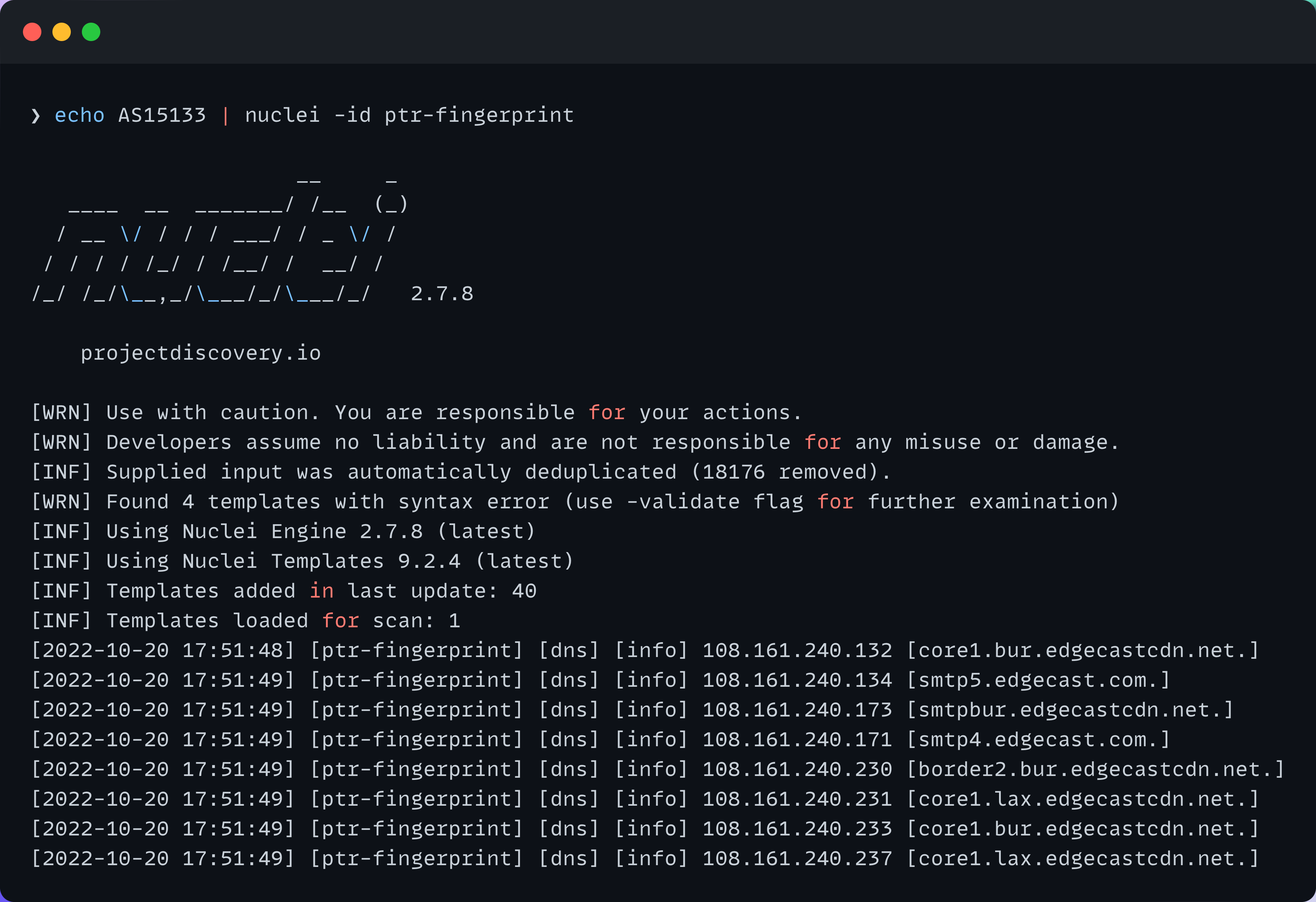
With the new release, Nuclei now supports ASN and CIDR as input. This means you don't even have to think about piping AS number mappings from asnmap to Nuclei.
For example:
Uncover Integration
What is Uncover?
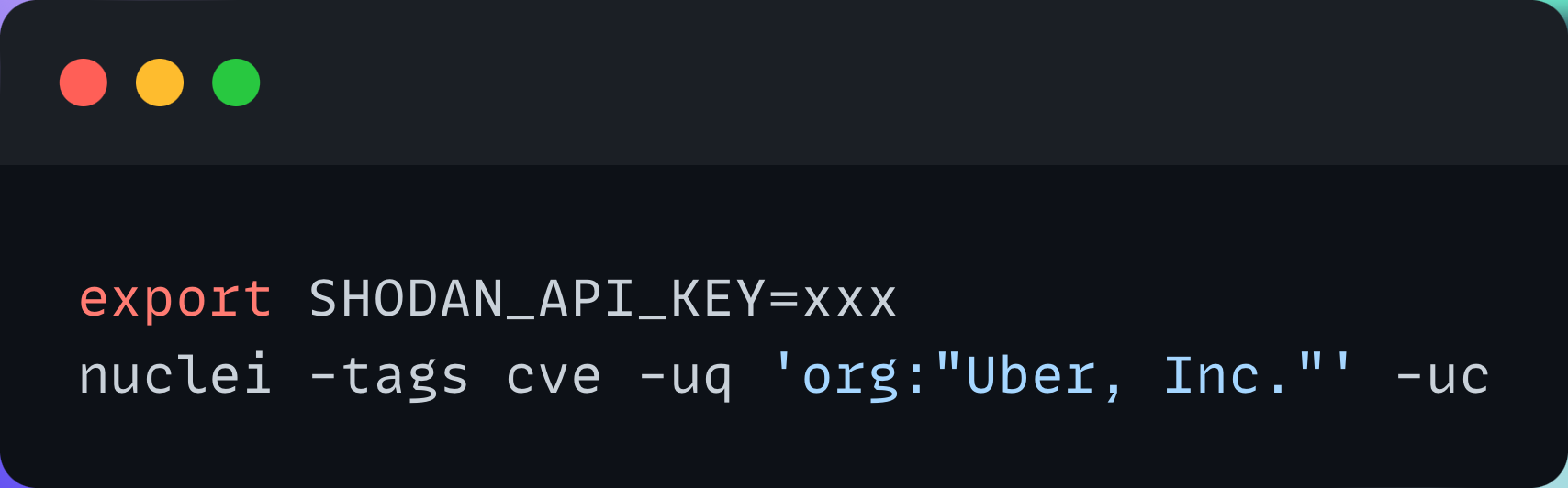
Uncover is a handy tool for searching passive reconnaissance services such as Shodan, Censys, and Fofa. It has a few handy flags such as the ability to search by company, and like all ProjectDiscovery tools, can be chained with many others for a quick reconnaissance workflow.
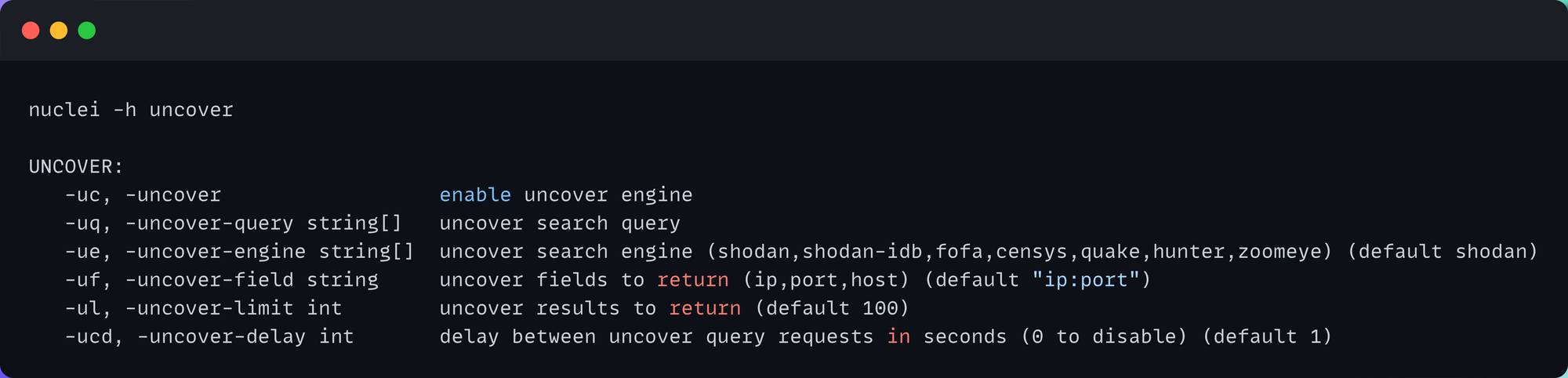
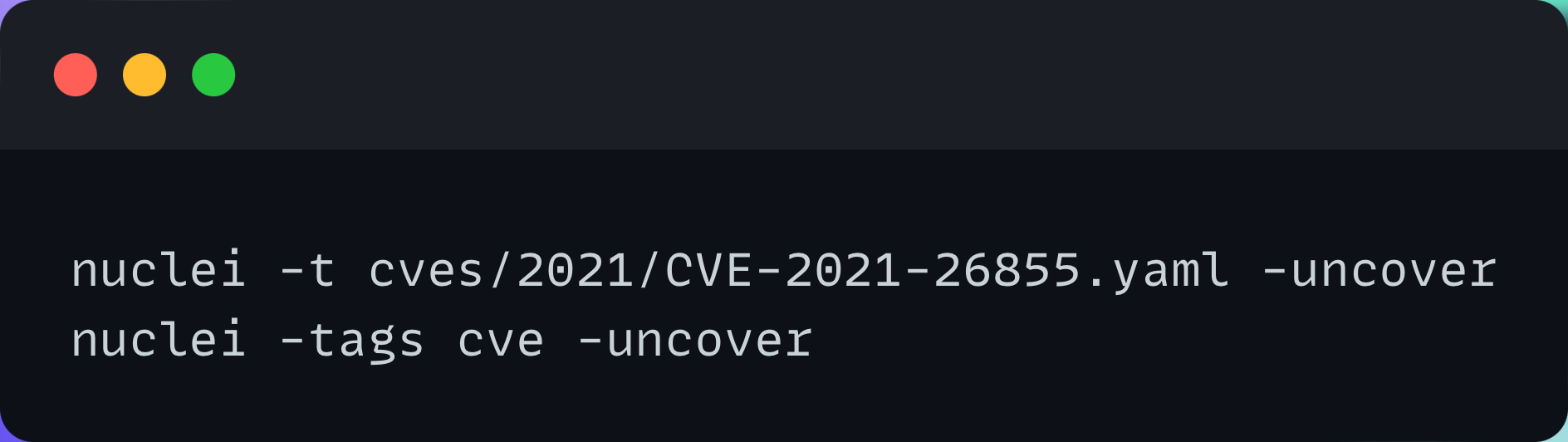
Nuclei now supports integration with uncover, which allows direct running of templates against hosts returned by uncover for the given query. See options for uncover below:
An example of template execution using a search query:
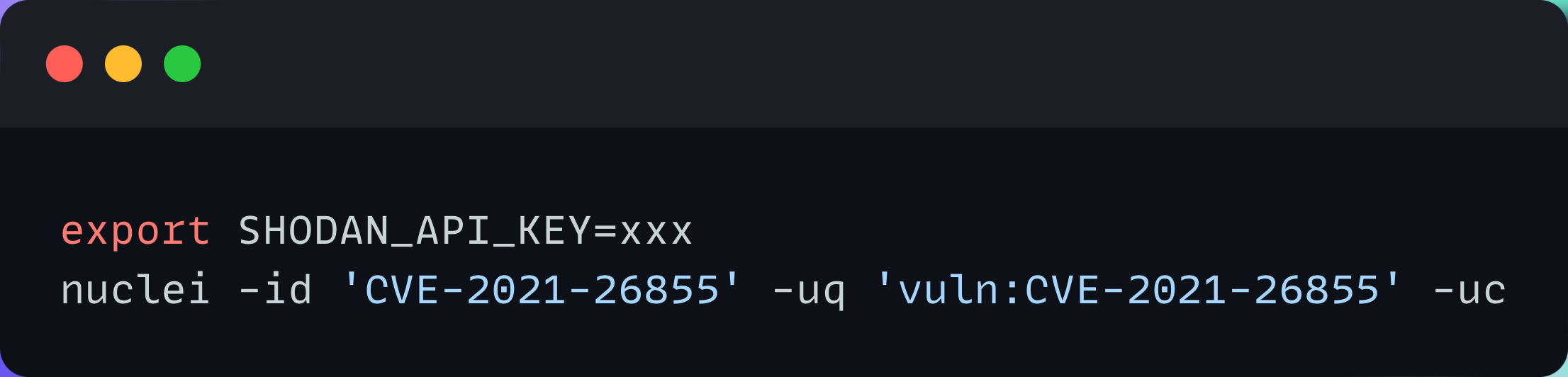
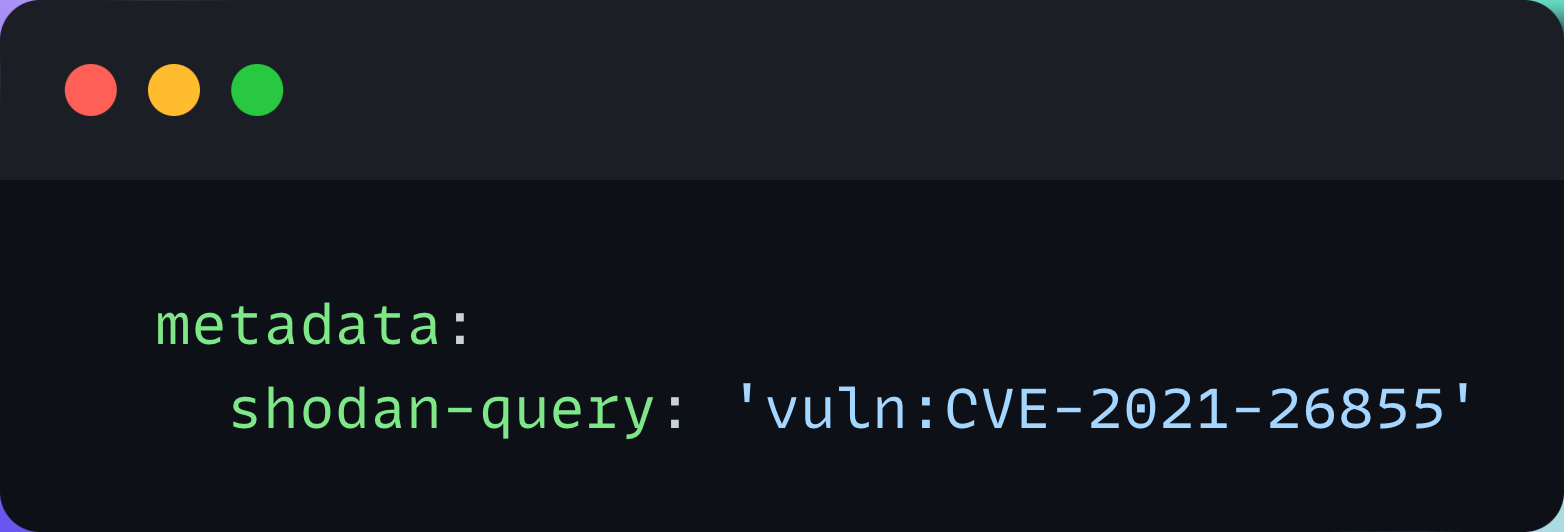
It can also read pre-defined queries from template metadata and execute templates against hosts returned by uncover for that query.
Here's an example of template execution using template-defined search queries:
httpx Integration
What is httpx?
httpx is a fast and multi-purpose HTTP toolkit that allows running multiple probes using the retryablehttp library. It is designed to maintain result reliability with an increased number of threads. It has the following features:
- Simple and modular code base making it easy to contribute.
- Fast And fully configurable flags to probe multiple elements.
- Supports multiple HTTP based probings.
- Smart auto fallback from https to http as default.
- Supports hosts, URLs and CIDR as input.
- Handles edge cases doing retries, backoffs etc for handling WAFs.
Previously, httpx probe data had to be piped to Nuclei. With httpx integration, this step can be entirely skipped!
This integration also means now nuclei engine automatically adopts the input and performs http probing depending on the type of templates you want to run.
For example, if you are running DNS or SSL templates, nuclei engine will skip the probing and use dns information as required and vice versa.
Running Nuclei with httpx piping:
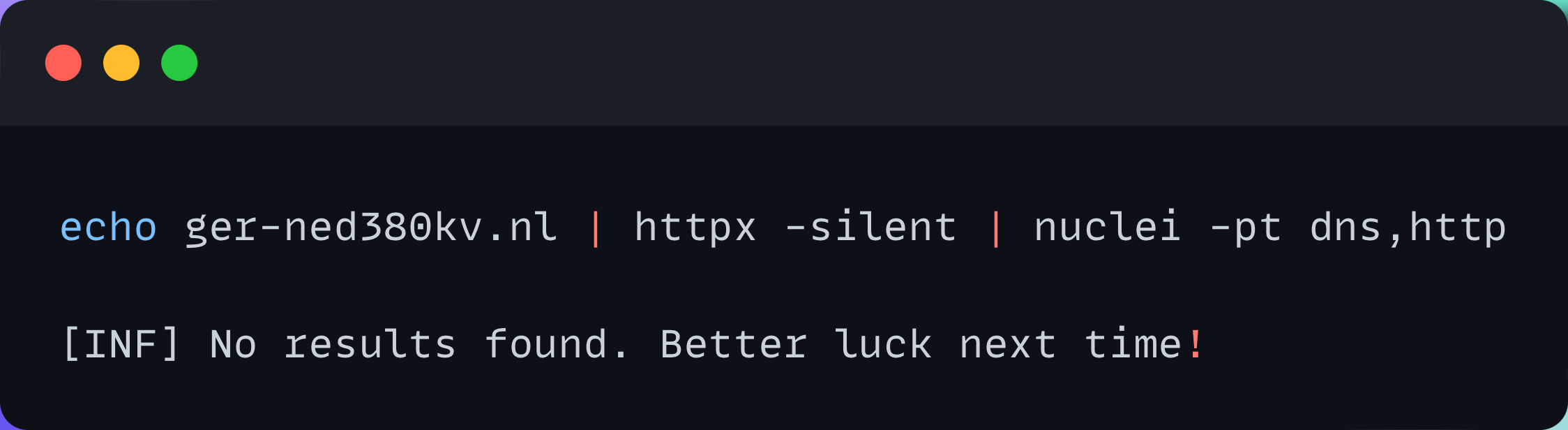
Running Nuclei httpx integration, without piping:
Custom template download support
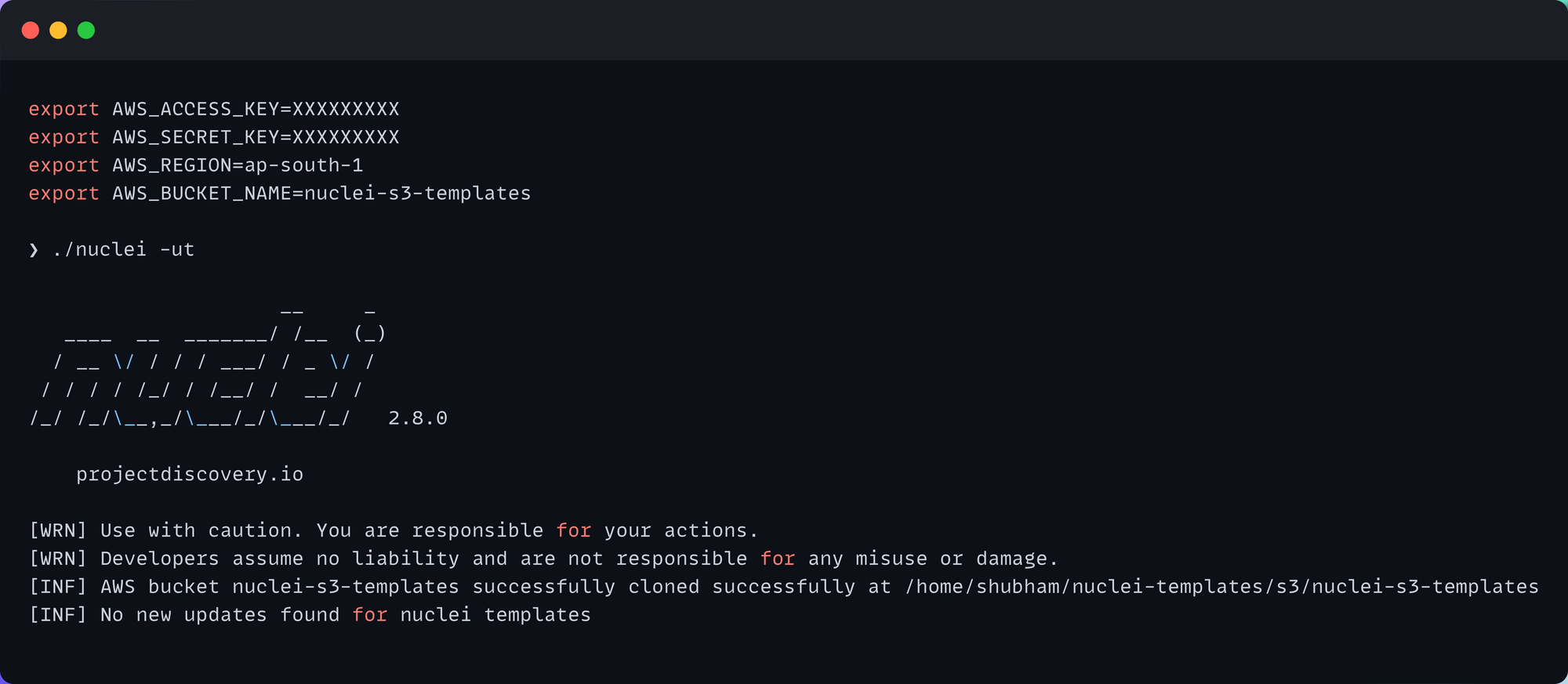
With Nuclei v2.8.0, you can now download/update custom templates from the following sources:
- GitHub
- AWS S3
Here is an example of downloading templates that reside in your AWS S3 bucket:
This release also contains many other features and fixes. To see other improvements in Nuclei v2.8.0, please visit the release milestone for more details.
That's all for this nuclei release; curious about what is coming next? here is a list of planned ideas that will be worked on and supported into future nuclei releases.
- Multi-protocol conditional matcher support;
- In template code/scripting support;
- Headless template simplification/enhancement;
- Extending newly added fuzzing support;
- Network protocol enhancement;
katana,subfinder,cloudlistintegration;- New protocol to support more automation
Feedback
- Using nuclei and got new features to suggest? please see the following discussion.
- Using nuclei and wanted to share how / where you are using it to prioritize features. please see the following discussion.
- New to nuclei or got questions to ask? Join the Discord server and follow on Twitter for updates.



