This guest post is by Rishi (aka rxerium).
Thanks for this post Rishi! If you have an idea for a blog post, reach out on our Discord server.
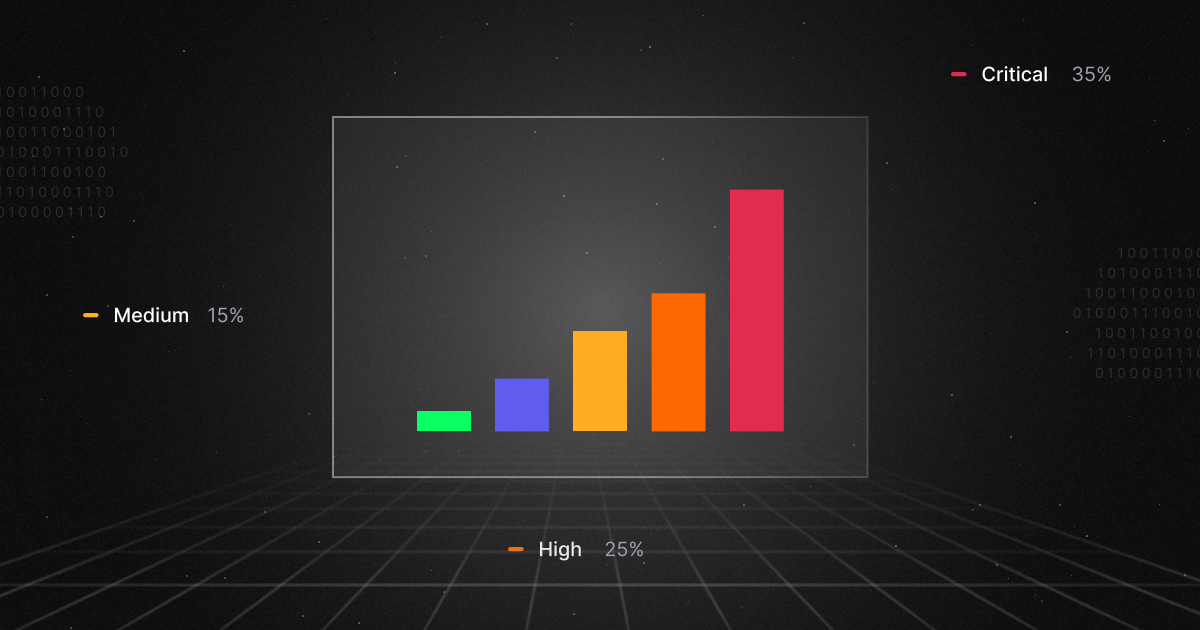
Escalating Threat: The Rise of Phishing Attacks
As a Cyber Risk Analyst at KYND, a cyber risk management company offering insights into the cyber posture for businesses of all sizes, I am always keeping up to date with the cyber threat landscape we face in the world today given the surge of cyber attacks following the conflicts in Russia and Ukraine and now in the Middle East. Adaptability is crucial given how rapidly events can take place when bad actors exploit systems and as they continuously come up with new attack techniques.
One of the growing concerns in the cyberspace is phishing as it remains the number one attack vector with 1.2% of all emails sent being malicious, which in numbers translates to 3.4 billion phishing emails daily (source). It is important to understand that attackers don't discriminate and are relentless in targeting individuals and organizations of all sizes, no matter where they are in the world.
When bad actors conduct phishing attacks, they often lure users to deceptive websites that look the same as legitimate ones except the domain will be different. These sites may prompt users to enter sensitive information like usernames, passwords, or personal identifiable information. Additionally, phishing websites might also present download pages, where users could inadvertently download viruses or malware onto their devices.
Phishing Website Detection Methods
Being a blue teamer, dedicated to protecting client infrastructure, I was researching various methods and techniques on how I could potentially detect these malicious websites both accurately and at scale through automation. Being a fond believer of open-source tools, I naturally turned to Nuclei as this was one of the main web scanning tools in my cybersecurity arsenal. Although Nuclei didn't support these templates initially, I opted to create them, as the process appeared straightforward given the simplicity of template creation.
Before embarking on this project I made a list of categories which I thought to be the most “targeted” in phishing attacks and they were:
- Banking / Financial sites
- Antivirus sites
- Shopping sites
- Password Manager sites
- Popular sites such as Google, Facebook, Amazon etc.
After consolidating the categories, I prompted AI to curate a list of the top 10-20 websites within each category. This built a foundation for me to then start writing Nuclei templates.
Template Creation Process
The template itself is quite simple, it sends a GET request to the provided host, then attempts to match on a phrase or a title in the page contents. If there is a match and the host does not match the real domain listed in the template (the legitimate one) then a possible phishing website has been detected.
Below is an example of a phishing template for Amazon:
id: amazon-phish
info:
name: Amazon phishing Detection
author: rxerium
severity: info
description: |
An amazon phishing website was detected
reference:
- https://amazon.com
tags: phishing,amazon,osint
http:
- method: GET
path:
- "{{BaseURL}}"
host-redirects: true
max-redirects: 2
matchers-condition: and
matchers:
- type: word
words:
- 'Amazon Sign In'
- 'Amazon Sign-In'
condition: or
- type: status
status:
- 200
- type: dsl
dsl:
- '!contains(host,"amazon.com")'
- '!contains(host,"amazon.co.uk")'
- '!contains(host,"amazon.co.es")'
- '!contains(host,"amazon.sg")'
- '!contains(host,"amazon.sa")'
- '!contains(host,"amazon.ca")'
- '!contains(host,"amazon.cn")'
- '!contains(host,"amazon.eg")'
- '!contains(host,"amazon.fr")'
- '!contains(host,"amazon.de")'
- '!contains(host,"amazon.in")'
- '!contains(host,"amazon.it")'
- '!contains(host,"amazon.co.jp")'
- '!contains(host,"amazon.pl")'
- '!contains(host,"amazon.se")'
- '!contains(host,"amazon.ae")'
condition: and
In certain cases during the template creation process, websites may only provide the site name within the title, potentially resulting in numerous false positives. To mitigate this, I matched both the title and the description of the website, offering a more robust approach to accuracy.
Running the templates through Nuclei
To put this into practice, I searched Shodan for potential phishing websites, in this example I used the query title:"Amazon Sign In", this allowed me to find hosts with “Amazon Sign In” present in the title, after finding
I created an input list, one containing the legitimate host (amazon.com) and the other containing a phishing website:
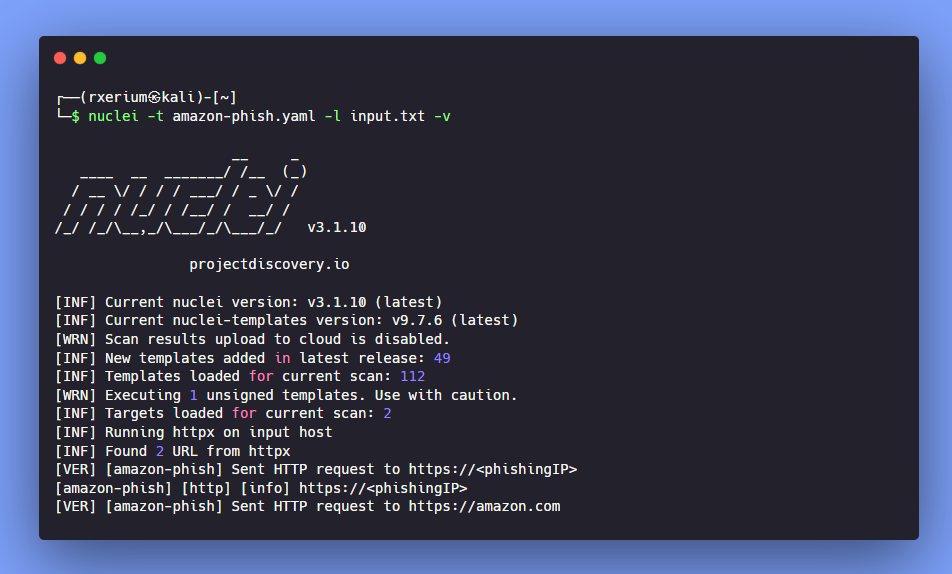
As you can see, it picked up the phishing website as expected.
Running all phishing templates through Nuclei is seamless and quick, the below scan took around 2 seconds to complete thanks to the default support for template clustering in Nuclei.
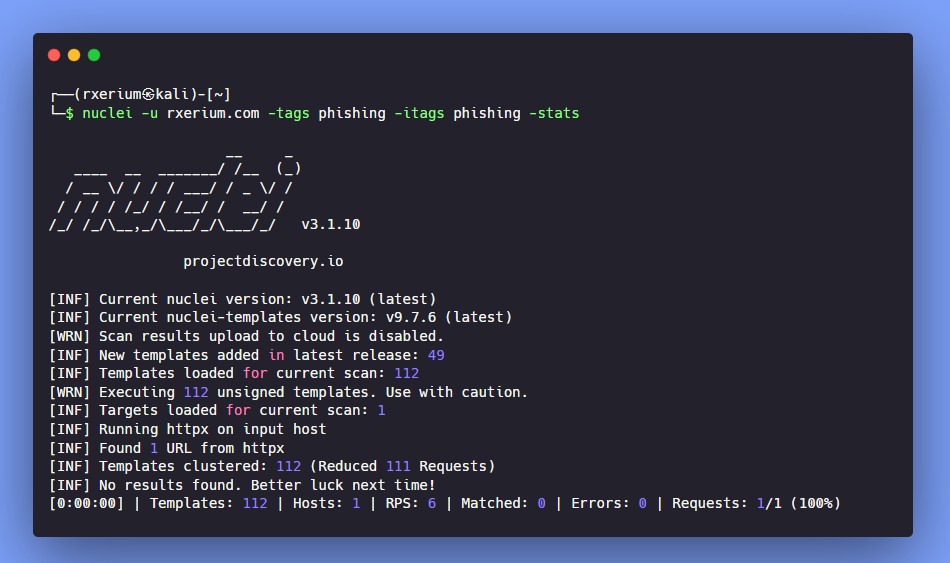
Note: These templates are not run in the default Nuclei scan. Users need to provide the -itags phishing option to include the phishing tag while scanning, or they can simply use the OSINT scan profile.You can either specify a OSINT config profile to run phishing templates along with other OSINT templates.
nuclei -u rxerium.com -config ~/nuclei-templates/config/osint.yml -statsUse Cases
For those involved in threat analysis, these templates can be useful. Here's where it gets really interesting for the Open Source Intelligence (OSINT) folks. These templates are not just about blocking or detecting; they're about gathering intelligence. By identifying and analysing phishing sites, OSINT analysts can uncover patterns, track threat actors' activities, and gather data that can be crucial for broader security research or investigative journalism. It's a useful addition in the OSINT toolkit.
Conclusion
These templates are released in Nuclei Templates v9.7.8 [Fishing for Phishing]. If you encounter false positives or have any suggestions, feel free to create a GitHub issue. Now, while we've an initial 113 Detection templates available to scan for phishing websites, I anticipate this number will expand as the security community continues to contribute and collaborate.
Try the phishing templates out for yourself here: