🎃Happy Halloween, PD community! The team are back again this month to share our latest developments, updates and releases we’ve been working on, as well as news from across the cybersecurity space. Of course, this October also saw the return of Hacktoberfest, and we couldn’t be happier with the turnout. Thank you all so much for your contributions!
We’ve been hard at work creating new content for you and adding more people to our Pioneers program. As always, we love to see your contributions and celebrating wins with you, so if you’re interested in joining our Pioneers, head to the Highlights section of this newsletter to find out more.
Our GitHub and Discord are always open for community members to join, share their thoughts and projects, and troubleshoot with the ProjectDiscovery team directly. Don’t hesitate to dive in, we’re looking forward to meeting you!
Release notes
nuclei v3.3.5
Version 3.3.5 of nuclei added new features in the form of support for several templates, including MongoDB for results reporting, stop-at-first-match in network templates, and global matchers and extractors in http templates.
A few bug fixes were also released, addressing issues with {{interactsh-url}} replacement in network templates, multipart fuzzing and support for filename and content-type in multiparts, and exposing SSL part definitions.
tlsx v1.1.8
The latest tlsx release was a minor update, which included a bump for the utils version.
httpx v1.6.9
In httpx this month, we’ve added support to filter out duplicate responses, and team-id input support for dashboard upload.
An issue was fixed where failed probe responses were not being stored, and an option was added to provide PDCP auth via a config file.
katana v1.1.1
This month’s katana update includes breaking news for Passive Crawling capability - v1.1.1 removes this completely, and will be released separately at a later date.
Alongside this, a few new features and enhancements were added, including the no-clobber flag to prevent overwriting of local files, and the -store-field-dir flag to make per-host field directories optional.
Several existing bugs were also fixed, including improper logging configuration and an issue where ctrl-c could not terminate the process in headless mode with the -show-browser option.
Nuclei Templates
July stats
Our major Nuclei Templates release this month was v10.0.2. Alongside bug fixes, enhanced detection for false negatives, and fixes for false positives, we’ve also gained 68 new templates, 5 first-time contributors, and 30 new CVEs!
Some highlights worth noting in this release address a SAML authentication bypass in GitLab, an SQL injection vulnerability for Palo Alto Expedition, and cross-site scripting in the WordPress Ninja Forms plugin.
A parsing issue was also fixed in the WordPress-WP-Mail-Logging template, and enhancements were added to update Fumengyun-SQLi for better detection, as well as a Strapi template being refactored for efficiency.
Huge thanks to our contributors on all of these releases - @kchason, @alban-stourbe-wmx, @geeknik, @gy741, @s4e-io, @KoYejune0302, @cheoljun99, @sim4110, @taielab, @1337rokudenashi, @sujal , @rxerium, @Mys7ic, @righettod, @r3naissance and @0xPugal.
And, congratulations to our first-time contributors: @vil02, @dany74q, @iuliu8899, @michael2to3, @zy9ard3, @eveneast, @ShuBo6, @o6uoq, @zrquan, @fmuttis, @dualfade, @stvnhrlnd, @KoratSec, @ShaneIan, @evilgensec and @aviadavi.
Other news
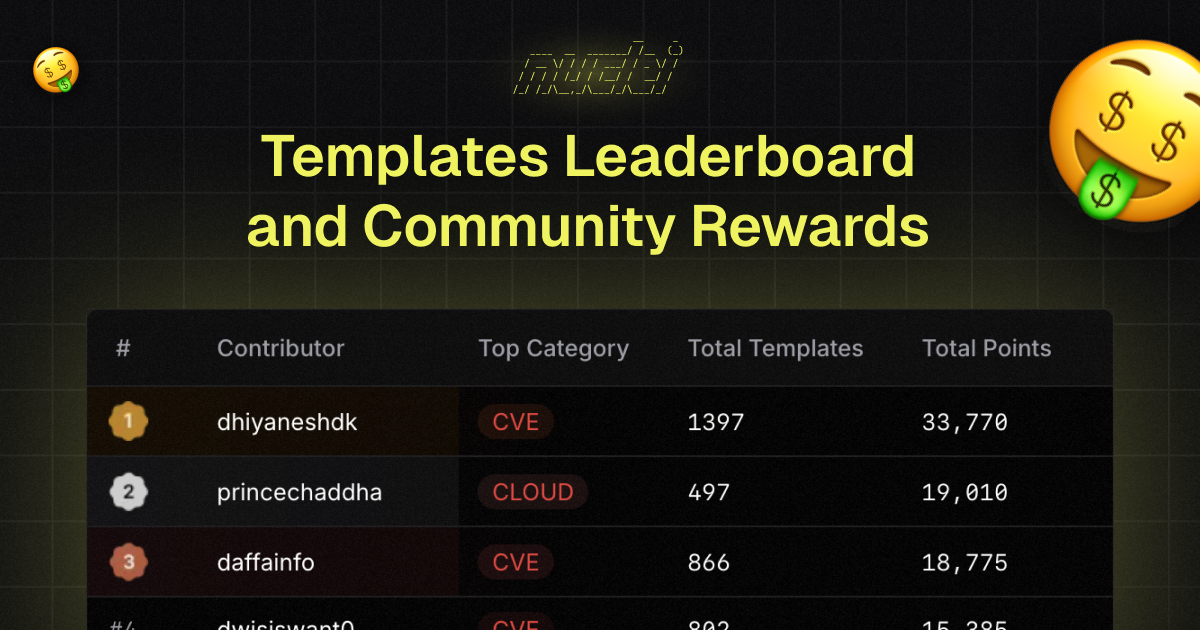
ProjectDiscovery’s Template Reward and Community Leaderboard Programs
Newly launched this month, our Template Reward and Community Leaderboard programs celebrate a huge milestone for the ProjectDiscovery community.
With over 9,000 stars and 900 unique contributors on our templates project, and 20,000 stars on the Nuclei repository, it felt like a natural next step for us to build a way to celebrate and showcase all of your hard work.
See the live leaderboard and to take part in our Template Rewards, check out any issues in our GitHub repository labelled with 💎 Bounty .
Once again, thank you so much for all of your contributions, and for making ProjectDiscovery’s tools some of the most innovative in the cybersecurity arena.
Highlights
PD Go Developer Tarun Koyalwar and AppSec Researcher Dhiyaneshwaran Balas spoke at BSides Ahmedabad this month, covering ‘Vulnerability Scanning and Enumeration with Nuclei: Deep Dive.’
ProjectDiscovery was also named Open Source Tool of the Year! https://x.com/bsidesahmedabad/status/1842097186114245022
Hacktoberfest 2024 was a huge success! You can check out all of our submissions over in GitHub: https://github.com/projectdiscovery/nuclei-templates/labels/Hacktoberfest
The bug bounty podcast Critical Thinking had a fascinating conversation around our published blog post on GitLab Authentication Bypass. https://www.youtube.com/watch?v=nxvqnNfwfz4&t=442s
Our first monthly PD Tips and Tricks video is available over on our YouTube channel: https://youtu.be/sJk6LtfDxGY?si=ICsyZRNtUF65uMM8
Intigriti noted that Nuclei can also be used for CVE scanning! https://x.com/intigriti/status/1844322239547834706
The first members of our Pioneers ambassador program have started to receive their swag packages. Check out the new design right here! https://x.com/thebinarybot/status/1845769347500781738
And if you’re interested in becoming a Pioneer too, it’s never too late. Head here to sign up: https://projectdiscovery.io/pioneers
Bash Bunny highlighted ChaosAPI - noting that using it allowed them to find more subdomains than just using subfinder! https://x.com/_BashBunny_/status/1846478187347550427
https://www.linux-community.de/wp-content/uploads/2024/11/lu-ce_2024-11.pdf - featured in German Linux User magazine
How do you hack NASA? Angry Oval Egg wrote about their experience through 7,380 subdomains: https://medium.com/@angryovalegg/hacking-nasa-a-journey-through-7-380-subdomains-9cc65e683fd7
https://www.linkedin.com/posts/activity-7253541971464466432-BMwd - Sean Murphy celebrated our new Template Reward and Community Leaderboard initiatives: https://medium.com/@angryovalegg/hacking-nasa-a-journey-through-7-380-subdomains-9cc65e683fd7
Join our community
Our diverse community spans members from full-time bug bounty hunters to Fortune 500 security engineers. Let's go!
Thanks,
The ProjectDiscovery Team
Have news you want to share with our community? Let us know